Security

A recent linked-wallet dump of PUMP tokens exposed how concentrated tokenomics and coordinated wallets create asymmetric exit risk. This article explains how to spot linked-wallet behavior, practical safeguards for traders and projects, and market lessons as capital rotates toward Bitcoin.
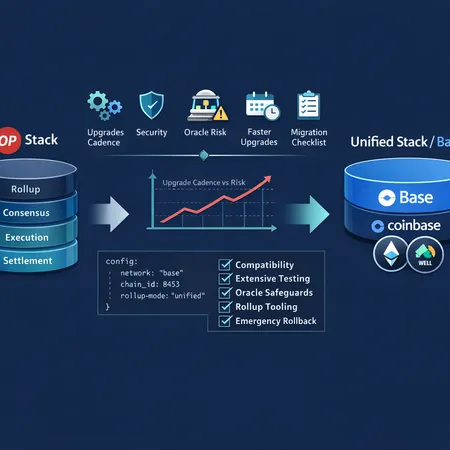
Coinbase-backed Base is moving off the OP Stack into a unified stack to accelerate upgrades and tighten security. This article explains why the change is happening now, what it means for tooling and rollups, and provides a practical checklist for teams on Base.
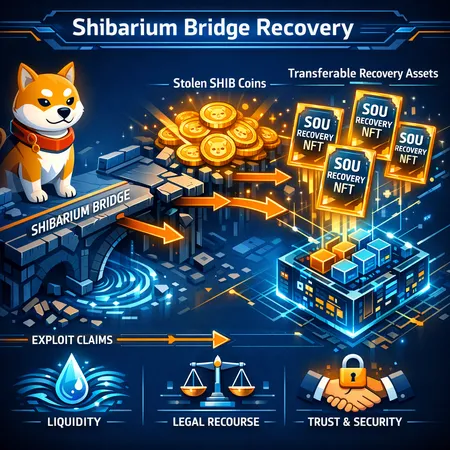
Shiba Inu’s SOU recovery framework has launched to convert bridge-exploit claims into transferable on-chain assets. This article explains the recovery-NFT mechanism, evaluates outcomes for users and the ecosystem, and places the approach in the wider context of bridge security and remediation best practices.

Three recent security incidents — malicious packages targeting dYdX users, Bithumb’s accidental 2,000 BTC distribution, and a 751M FUN transfer to Binance — illustrate different faces of custody and protocol risk. This feature breaks down technical mechanics, trader signals from large on‑chain deposits, mitigation checklists, and policy implications for regulators and exchanges.

A detailed post‑mortem of the Step Finance treasury breach that drained roughly $27–30M in SOL, why the STEP token collapsed, and concrete hardening measures DeFi projects should adopt to protect treasuries.

This piece weighs Michael Saylor’s warning that protocol mutability is Bitcoin’s greatest risk against the quantum-computing narrative, assessing engineering trade-offs, developer activity, and sensible priorities for custodians and node operators.

Active traders face a clustered set of risks — technical, derivatives, security, and market-structure — that can compress BTC quickly. This piece breaks down seven immediate threats and gives concrete hedge strategies and a monitoring checklist to survive a volatile drawdown.

A deep-dive into the ~$280M hardware-wallet theft that routed funds into Monero via THORChain, the attack vectors used, and actionable custody and policy steps security officers and family offices should adopt.
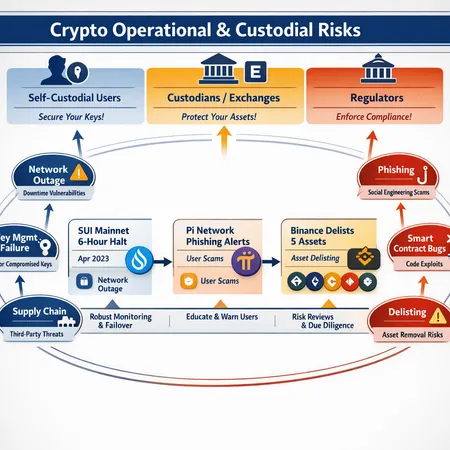
A deep investigation into how recent incidents — the Sui mainnet halt, Pi Network phishing alerts, and Binance support cuts — reveal the evolving attack surface for users and custodians. Practical controls, exchange decision drivers, and a regulatory checklist for hardening operations are provided.
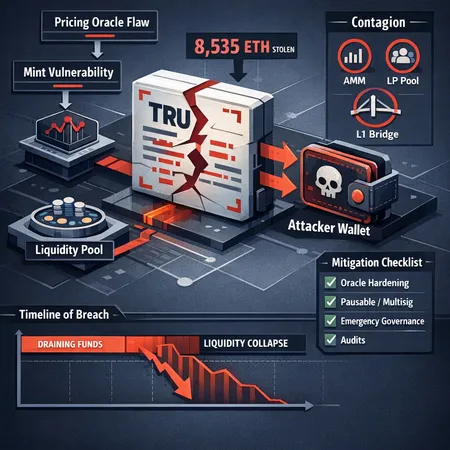
A technical post-mortem of the Truebit (TRU) exploit that allowed minting via a pricing-oracle flaw and led to a 8,535 ETH ($26M) liquidity drain and near-total collapse of TRU. This article breaks down the exploit mechanics, timeline, contagion risks for AMMs and pools, and a practical remediation checklist for DeFi teams.