Operational and Custodial Risks in Crypto: Mapping Outages, Phishing, and Delistings
Summary
Overview: why these incidents matter now
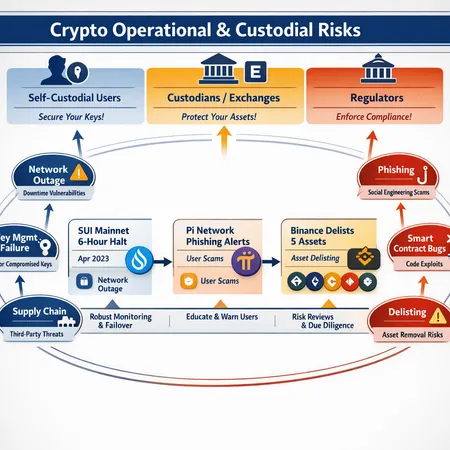
The last several weeks crystallized a familiar but dangerous truth: crypto's attack surface is no longer just smart-contract bugs. It includes network outages, targeted social engineering campaigns, and the operational choices of large custodians and exchanges. When a mainnet pauses for hours, when projects warn users about phishing as they approach open mainnet, or when an exchange removes support for assets on certain networks, users and custodians can suddenly lose access, value, or trust. This investigation synthesizes three recent threads — the Sui six‑hour mainnet halt, Pi Network phishing alerts, and Binance cutting support for five assets — and places them against a broader record of custody-related fraud and compliance failures.
For security and compliance officers, self-custodial users, and exchange operators, this is a practical map of where threats are concentrated and what to do about them. Along the way I reference public post-mortems and announcements so you can follow the facts and implement mitigations.
Recent incidents: timelines and key facts
Sui mainnet halt (SUI) — a six‑hour outage
On a recent day Sui’s mainnet experienced a multi‑hour halt that halted block production and user activity. The Sui developer team published a post‑mortem explaining the incident and stressing that wallets and funds were not lost during the pause; they attributed the disruption to a consensus-related failure triggered by a particular set of node conditions and coordination issues during recovery. The team's writeup provides the operational timeline and steps taken to bootstrap the network back to healthy state (Sui post‑mortem).
Why it matters: even when balances are intact, a prolonged outage erodes trust, prevents trading and liquidations, and can cascade into price and margin events on exchanges that support SUI.
Pi Network phishing alert (PI) — social engineering as a launch risk
As PI moved toward open mainnet, the project issued public security advisories warning users of sophisticated phishing attempts targeting onboarding users and key‑recovery flows. The alert emphasized that attackers were using fake apps, impersonated domains, and social media scams to harvest credentials and recovery phrases (Pi Network security alert).
Why it matters: new mainnets and token launches are high‑traffic moments when inexperienced users are especially vulnerable. Phishing at scale can turn onboarding events into mass custody failures.
Binance cuts support for five assets — operational and custody access impacts
Binance announced it would cut support for five popular cryptocurrencies on certain networks, citing technical and operational reasons. Such moves, whether motivated by security, liquidity, or compliance concerns, immediately change custody and withdrawal pathways for users and can strand assets when alternate rails are limited (Binance support cuts).
Why it matters: delistings or network support removals shift custody responsibility back to users or other custodians. They also spotlight how centralized exchange policies can create systemic access risk.
Enforcement and fraud — a cautionary backdrop
Operational and custody failures are not only technical. Recent criminal sentences, such as the 3‑year prison term imposed on the founder of an unlicensed crypto academy for a $2.9M fraud, underline how poor operational controls and misleading custody promises create consumer harm and enforcement risk (Brian Sewell case).
Why it matters: custodial promises without audited controls, transparency, or licensing invite fraud and regulatory action — another vector by which users lose assets.
Root causes: what these incidents reveal about systemic weaknesses
A pattern emerges when you join the dots: the same categories of failure recur across projects and intermediaries.
Technical fragility in consensus or client implementations. The Sui halt highlights how protocol edge cases or poorly handled state transitions can pause a network even when funds remain technically intact. Insufficient chaos testing and limited validator diversity increase this fragility.
Centralized operational chokepoints. Many blockchains rely on a small set of validators, bridges, or RPC providers; when one fails, users downstream see outages or degraded service. Exchanges depend on node operators and bridge services to keep custody flowing.
Social engineering and onboarding risk. Projects entering open mainnet like PI are prime targets for phishing. Attackers exploit brand recognition, rushed onboarding UX, and user naivety.
Policy and liquidity decisions at exchanges. Delistings and support changes are driven by security concerns, low liquidity, or regulatory pressure. Those decisions can strand retail users who lack self‑custody readiness.
Weak institutional controls and fraud risk. Unlicensed custodians or services without audited segregation of customer assets expose users to misappropriation, as the Brian Sewell case illustrates.
How exchanges decide delistings and support cuts
Exchanges weigh multiple, often competing factors before removing support for an asset or a specific network:
- Security posture of the chain and recent incidents (repeated consensus failures, unrecoverable forks, or exploit history).
- Liquidity and market depth: low‑volume markets are costly to operate and easier to manipulate.
- Technical complexity and maintenance cost: supporting multiple networks for the same ticker (for example, ETH across layer 2s) requires running extra infrastructure and monitoring.
- Regulatory and compliance pressure: ambiguous legal status, sanctions risk, or law‑enforcement concerns can force delistings.
- Custodial risk and bridge safety: assets that rely on fragile bridges or single custodians raise counterparty risk.
When public exchanges act, they balance user access versus platform stability and legal exposure. The Binance announcement showed that even large exchanges will shrink supported rails when the operational cost or compliance profile changes (Binance cuts support).
Mapping the attack surface for users and custodians
Think of the attack surface in layers:
- Network and consensus layer: outages, chain halts, replay/fork risks (SUI example).
- Client and wallet layer: compromised clients, malicious updates, insecure seed storage, phishing (PI example).
- Bridge and cross‑chain layer: custody ambiguity, wrapped asset risk, and rugging of bridge liquidity.
- Exchange/custodian operations: key management failures, insider theft, inadequate segregation, delisting policy shocks.
- Regulatory and legal layer: enforcement actions that freeze or change access to assets, and inconsistent disclosure requirements.
All of these interact. A network outage can trigger margin calls on exchanges, which in turn raise liquidity and custody stress. A phishing campaign can empty user wallets precisely when an exchange tightens withdrawals — compounding losses.
Best practices: what custodians and self‑custodial users should do
Below are prioritized, actionable controls. They are intentionally practical for security and compliance teams as well as advanced self‑custodial users.
For custodians and exchanges
Harden key management: enforce cold/hot split, use multi‑party computation (MPC) or hardware security modules (HSMs), and require multi‑sig for high value moves. Rotate and rekey on a controlled cadence.
Diversify infrastructure: run nodes across clouds, regions, and multiple RPC providers; do not rely on a single bridge or validator operator.
Formal incident response and communication playbooks: define RTO/RPO targets, escalation paths, and clear customer notification templates to avoid panic and misinformation during outages.
Regular third‑party audits and penetration tests: include proofs of reserve (with cryptographic evidence where possible) and publish scope and limitations.
Chaos engineering and pre‑mortems: simulate chain halts, transaction storms, and node compromises. The Sui event shows the value of rehearsed recovery.
Delisting governance: document criteria for delisting/support withdrawal and publish timelines and user remediation guidance well in advance.
For wallet users and self‑custodians
Prefer hardware wallets and multi‑sig for significant balances. For everyday use, segregate funds: keep a small hot wallet, store the rest cold.
Verify domains/apps and use bookmarked official sources. Projects nearing mainnet will be heavily targeted; follow official channels and double‑check links. The Pi Network advisory demonstrates how launch phases amplify phishing risk (Pi Network alert).
Learn to move across rails safely: if an exchange delists a network for ETH or another token, understand bridge alternatives and on‑chain liquidity before initiating transfers.
Use on‑chain proofs and block explorers to validate transactions; keep recovery phrases offline and never share them.
Have a plan for delistings: know how to export custody, find alternative custodians, or use decentralized bridges with due diligence.
A regulatory lens: minimum standards to reduce systemic custody risk
Regulators and industry bodies can reduce harm while preserving innovation by focusing on operational resilience and transparency rather than outright bans. Proposed minimums:
Mandatory incident reporting. Require exchanges and custodians to report major outages, thefts, and delistings within a strict timeframe with a public summary.
Minimum custody controls. Adopt baseline technical standards analogous to SOC2 or the traditional custody framework: audited cold/hot separation, multi‑sig or MPC, and periodic key custody proofing.
Transparency around delisting criteria. Exchanges should publish the rationale, timeline, and user remediation steps to prevent confusion and panic selling.
Standards for onboarding and wallet UX. Projects launching mainnet should be required to publish secure onboarding guides and phishing advisories; regulators can partner with projects to fund public education campaigns.
Consumer protection and insurance backstops. Custodial services should either hold backed reserves or obtain insurance that covers operational failures and fraud, with clear claim procedures.
Licensing and enforcement. The Brian Sewell sentencing is a reminder that misrepresentations about custody must be enforceable with timely regulatory oversight and criminal penalties for fraud (Sewell case).
These standards should be risk‑based: higher assurance for institutions that custody third‑party assets and lighter requirements for bona fide self‑custody tooling.
Practical checklist (for teams and users)
- Custodians/exchanges: implement MPC or multi‑sig, diversify nodes, run chaos tests quarterly, publish delisting policy, and maintain an incident playbook.
- Security/compliance officers: require third‑party audits, proof of reserves, and timely incident reporting from service providers; map dependency graphs (RPC, bridges, validators).
- Self‑custodial users: use hardware wallets, split funds, verify onboarding sources, and maintain an evacuation plan if a preferred exchange delists a network.
Platforms such as Bitlet.app and other service providers increasingly emphasize some of these controls; however, users and teams must still verify each provider's specific practices rather than relying on branding alone.
Conclusion: hardening for a more resilient ecosystem
Network outages like the Sui halt, phishing surges around projects like PI, exchange policy changes from major platforms, and classic custody frauds together show that custody risk is multi‑dimensional. Mitigations require both technical controls (MPC, multi‑sig, diversified nodes) and governance improvements (transparent delisting policies, mandatory incident reporting, and minimum custody standards).
Security and compliance officers should treat these events as data points, not anomalies: build them into tabletop exercises, insist on audited controls from partners, and educate users against phishing. Self‑custodial users must accept responsibility for protecting keys while preparing contingency plans for exchange delistings.
The ecosystem will not eradicate risk, but with disciplined operational practices and clearer regulatory baselines, we can make custody failures less frequent and less catastrophic.
Sources
- Sui mainnet halt and developer post‑mortem: https://www.coinspeaker.com/sui-blockchain-explains-major-outage-claims-funds-were-safe/
- Pi Network security alert: https://en.cryptonomist.ch/2026/01/16/pi-network-security-alert/
- Binance cuts support for five cryptocurrencies: https://u.today/binance-cuts-support-for-five-popular-cryptocurrencies-ethereum-meme-coins-and-defi-in-focus?utm_source=snapi
- Brian Sewell sentencing and custody fraud case: https://crypto.news/american-bitcoin-academy-founder-brian-sewell-gets-3-years-for-2-9m-crypto-fraud/