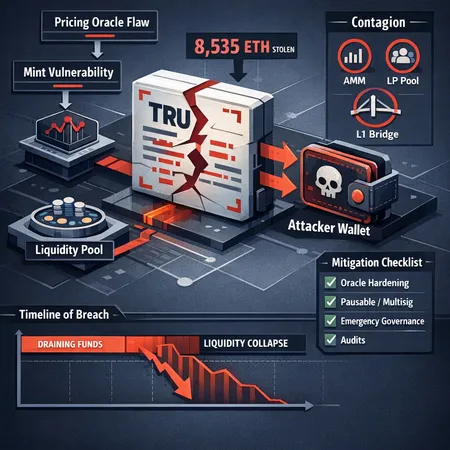
Post-mortem: Truebit (TRU) exploit that drained ~8,535 ETH — technical analysis & remediation
Summary
Executive summary
In early 2026 Truebit's TRU token suffered a major exploit: an attacker leveraged a pricing oracle / contract logic flaw to mint an outsized amount of TRU, then swapped that supply into ETH on on-chain automated market makers (AMMs), draining about 8,535 ETH (≈ $26M) and sending TRU to near-zero. Multiple post-incident writeups attribute the root cause to a pricing/minting vector in legacy contract logic that allowed creation of tokens without proper collateralization. Sources confirming and describing the mechanics include reporting from TheNewsCrypto, CoinSpeaker, CryptoPotato, and DailyCoin.
This post-mortem is written for DeFi developers, security engineers and token holders. It covers: the exploit mechanics as reported; a timeline of the drain and liquidity collapse; why legacy contract design is a systemic risk; short-term contagion vectors for pools and L1 liquidity; and a practical remediation checklist (technical mitigations and governance/response steps).
Background and the vulnerable assumptions
Truebit’s token economics and minting controls relied in part on an on-chain pricing calculation tied to AMM reserves or an internal price function. According to public reporting, a miscalculated on‑chain price (a pricing oracle flaw) and insufficient validation around minting arithmetic allowed the attacker to mint TRU at a cost far below its market value, then swap it for ETH on liquidity pools, draining reserves.
Two key assumptions common in legacy DeFi contracts that appear relevant here: (1) on-chain instantaneous prices are safe to compute required minting/collateral amounts, and (2) internal sanity checks and caps are either absent or insufficient to handle flash-manipulation and extreme price slippage. Those assumptions are fragile against flash loans, MEV and direct pool manipulation.
Exploit mechanics — what the reports show
High-level sequence reported across investigators:
- The attacker found a pricing/minting vector in Truebit’s smart-contract logic that derived required mint/collateral amounts from on-chain price data or AMM reserves without robust smoothing or bounds. See coverage by CryptoPotato and CoinSpeaker for technical summaries.
- Using that flaw, the attacker minted a large quantity of TRU essentially at a discount (or without the expected backing). CryptoPotato describes the exploit as enabling unauthorized minting and draining of ETH reserves; CoinSpeaker notes the token rapidly lost value after the exploit.
- The attacker immediately swapped newly minted TRU on one or more AMMs, executing large sell pressure that removed ETH liquidity from pools and cascaded slippage; DailyCoin and TheNewsCrypto document how swaps drained pool reserves and crushed TRU price.
Two properties made this efficient for the attacker:
- Atomic flash-style execution: minting and swapping can be executed inside a single transaction (or tightly chained transactions) so that price manipulation or oracle attacks cannot be externally countered before settlement.
- Weak price oracle design: on-chain price sampling from a single, mutable liquidity pool or naive reserve math is easy to manipulate with enough capital or flash loans.
Where the public coverage stops short is in low-level bytecode specifics; investigators are still piecing together exact function calls and arithmetic edge-cases. For immediate defensive purposes, however, the functional story is clear: a mint vulnerability combined with an on-chain pricing flaw led to a liquidity drain. (See TheNewsCrypto, CoinSpeaker, CryptoPotato, DailyCoin.)
Timeline: how the drain unfolded (reported sequence)
Phase 1 — reconnaissance and exploit trigger: the attacker identified the pricing calculation/mint function and crafted transactions to produce an advantageous price readout or bypass arithmetic checks.
Phase 2 — mass mint and swap: the attacker minted a massive TRU balance and routed swaps through AMMs, converting TRU to ETH at escalating slippage. This occurred quickly and in repeated transactions to maximize extraction before any human response.
Phase 3 — pool exhaustion and price collapse: targeted liquidity pools lost significant ETH reserves (~8,535 ETH total reported) and TRU liquidity evaporated, sending the token price to effectively zero as LPs withdrew or were washed out.
Phase 4 — post-exploit reaction: exchanges, builders, and liquidity providers started isolating pools, freezing UI front-ends, and issuing advisories. Public reporting followed within hours and investigators began tracing flows to identify the attacker’s exit points.
Exact timestamps and tx hashes should be referenced from on-chain forensic reports; the assembled narrative above reflects the consolidated coverage in linked reports.
Immediate impact and contagion risks
The exploit’s direct consequence was the loss of ETH liquidity and a near-total collapse of TRU price. But the secondary risks are the more dangerous part for DeFi infrastructure:
Pools and AMMs: LPs in pools with TRU saw impermanent loss and potential insolvency as the pool asset became toxic. Attack-driven slippage can cascade into other token pools that route through the same pairs.
L1 liquidity and routing: large drains of ETH from on-chain liquidity reduce available routing options and may force arbitrageurs to shift liquidity; in stressed markets this can elevate slippage across unrelated pairs.
Bridges and wrapped assets: if TRU were bridged to other chains, the exploit could create cross-chain contagion as wrapped TRU loses peg and counterparties freeze operations.
Counterparty and protocol exposure: lending platforms, collateralized short positions, or automated strategies holding TRU will suffer losses or liquidations, potentially leading to collateral calls and broader market stress.
Because many DeFi systems assume composability, a single exploited token can create a domino effect — a core reason why legacy contract logic that trusts instantaneous on-chain math is systemic risk.
Why legacy contract logic remains a systemic risk
Several systemic design anti-patterns common in older DeFi contracts combined to enable this event:
Reliance on instantaneous spot price from a single AMM pair rather than time-weighted average price (TWAP) or robust oracle aggregates. Spot prices are manipulable within a transaction.
Missing or weak mint caps and lack of circuit-breakers: without mint ceilings, an exploiter can create unlimited supply if other checks fail.
Unsafely assuming invariants (reserve ratios, non-zero denominators, unchecked integer math) — legacy code sometimes omits edge-case math checks.
Poor emergency governance: slow multisignature or off-chain governance makes it impossible to react before a fast exploit finishes.
Upgrade patterns that centralize upgrade power without adequate checks (so upgrades can be rushed but also abused) or, conversely, immutable code that cannot be patched when a critical bug is found.
These structural issues make “legacy” contracts high‑risk building blocks in an ecosystem that prizes composability. The TRU incident is a reminder that contracts which once seemed safe can become single points of failure as on-chain capital and flash-loan tooling grow.
Practical technical mitigations (developer checklist)
Below is a prioritized checklist for teams building token minting or price-sensitive contracts.
Use robust price oracles
- Prefer decentralized or aggregate oracles (Chainlink, multiple AMM TWAPs) and implement minimum observation windows.
- Never compute required collateral purely from a single instantaneous AMM pair.
Add minting controls
- Hard caps per time window, per address and global supply ceilings.
- Rate limits and per-block or per-tx mint caps to prevent atomic flood minting.
Implement circuit-breakers and pausability
- A pausable pattern allows emergency halting by a defined multisig or governance process.
- Automatic circuit-breaker triggers for extreme price divergence, large single-address mints, or anomalous transfer volumes.
Harden financial math
- Use libraries like OpenZeppelin SafeMath (or integrated language safety) and assert expected invariants before state changes.
- Validate denominators, overflow/underflow cases, and decimal mismatches explicitly.
Reserve and collateral sanity checks
- Require multi-source collateral valuation and conservative haircuts on on-chain valuations.
- Avoid trusting self-reported reserves from a single contract.
Reduce atomic dependency surfaces
- Limit complex cross-contract logic in a single transaction where possible. Keep critical validations minimal and externalized to tested oracle contracts.
Use upgradeability with safeguards
- If using proxies, require multi-sig governance for upgrades and implement time-lock delays for admin-level changes.
Continuous monitoring and alerting
- Real-time monitors for large mints, large swaps, unusual slippage, and sudden balance changes. Integrate sentinel bots to pause or flag suspicious transactions.
Defensive liquidity management
- Require multisig or DAO approval for large liquidity additions/removals, and implement whitelist windows for new pools/pairs.
Governance and incident response playbook
Technical mitigation must be complemented by practical governance and IR processes:
Pre-define an incident response (IR) runbook
- Roles & escalation: who can pause, who communicates, who liaises with exchanges.
- On-chain actions: pause, revoke privileged roles if compromised, freeze bridge wrappers if possible.
Forensic triage
- Snapshot relevant block/state, trace attacker inflows/outflows (use on-chain explorers), identify exit AMMs and custody points. Coordinate with chain analytics firms if needed.
Communications
- Rapid, honest public communication reduces speculation. Publish initial findings, recommended user actions (e.g., withdraw liquidity, revoke approvals), and a timeline for fixes.
Coordinate with custodians & CEXs
- If attacker funds route to centralized exchanges, provide forensic evidence to request freezing of funds (where legally possible).
Governance remediation
- Patch the vulnerability through audited upgrades, but balance speed with security: deploy fixes to a testnet and audit the patch where feasible. Use timelocks and multisig to avoid rushed mistakes.
Post-incident review
- Publish a technical post-mortem, lessons learned, and compensatory plans for affected users (if any). External independent audit of the revised system is strongly recommended.
Short-term actions for LPs and AMMs exposed to TRU
If you are an LP or protocol with exposure:
- Immediately remove or reduce exposure where possible. If the pool UI is disabled, interact directly via contract calls to withdraw liquidity.
- Revoke approvals to token contracts showing unexpected behavior via wallet interfaces or tooling.
- Coordinate with other LPs and deploy governance proposals (if available) to pause affected pairs or delist the token until forensic work completes.
- If you run an AMM, consider adding logic that detects and rejects extreme price-impact trades originating from single addresses or with suspicious routing.
Longer-term lessons for the DeFi ecosystem
Composability is a strength—and a liability. Protocol designers must treat incoming token contracts as potentially hostile primitives and avoid trusting external contract invariants without validation.
Legacy code audit and remediation programs need funding and prioritization. Projects should inventory smart-contract risk, categorize contracts by exposure, and schedule upgrades where necessary.
Incident preparedness — from automated monitors to legal/coordinated freeze options — will determine whether an exploit becomes isolated or systemic.
Conclusion
The Truebit/TRU incident is a vivid reminder: pricing oracle flaws combined with mint vulnerabilities are catastrophic. The attacker’s path—minting unbacked supply then converting it into ETH via AMMs—relied on fundamental assumptions that no longer hold in a world of flash loans and MEV. For builders and token holders, the immediate priorities are hardened oracles, mint limits, circuit-breakers, and a clear IR playbook. Projects should treat legacy contract logic as an active liability and prioritize patched upgrades and monitoring.
Platforms and services across the ecosystem (including installment and P2P offerings such as Bitlet.app) must factor token-level risk into product exposure and underwriting models.
For further reading and to follow on-chain forensic details, see the investigative reporting linked in the Sources below. And if you maintain a token contract with minting power or on-chain pricing dependencies, assume you are a potential single point of failure until proven otherwise.