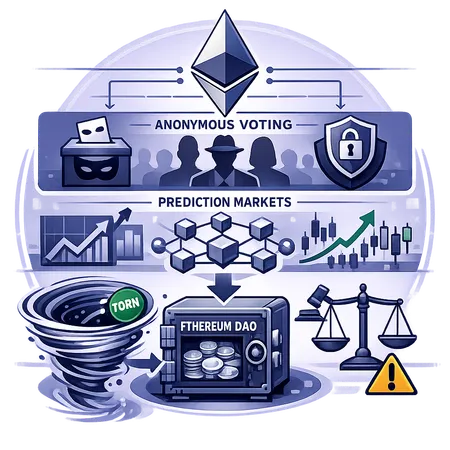
Privacy vs. Accountability: Ethereum’s Turn to Anonymous Voting and Tornado Cash–Funded DAO Risks
Summary
Why this moment matters
This is a pivotal moment for on-chain governance. Two signals collided in public view: Vitalik Buterin's shift toward a two-layer governance framework that explicitly embraces anonymous voting as a defensive tool, and an Ethereum DAO accepting a deposit with ties to Tornado Cash — a privacy protocol that regulators have flagged. Together they force DAO founders, governance researchers, and compliance officers to confront hard trade-offs between voter privacy, governance integrity, and legal exposure.
For context, Ethereum governance has evolved from ad hoc multisigs and social consensus to token-weighted on-chain voting, off-chain signaling, and experimental mechanisms. The new proposals and events deserve a calm, forensic look: what do the mechanisms claim to solve, where do they fall short, and which practical guardrails can preserve both privacy and accountability?
The two-layer proposal: anonymous voting plus prediction markets
At its core the two-layer proposal separates private expression from public forecasting.
- Layer 1: Anonymous voting — participants cast ballots without on-chain linkage to their identity or wallet. The aim is to prevent targeted harassment, coercion, and vote-buying tied to observable on-chain balances.
- Layer 2: Prediction markets — open, public markets that surface incentives and aggregated beliefs about proposal outcomes, actor motivations, and likely consequences.
The idea is elegant in principle: make the act of voting resistant to attack while leaving market signals visible to inform decision-making. Anonymous ballots protect the voter; prediction markets are a transparent, fungible mechanism that lets outsiders and the DAO itself assess the direction and confidence of the community.
How the two layers complement one another
Prediction markets act as an accountability layer that compensates for the opacity introduced by anonymous ballots. If votes are private, markets can show whether participants are willing to economically stake on a policy's predicted results. Together they aim to: reduce coercion, maintain signal fidelity, and deter blatant vote-selling because the market price provides an independent signal that can be compared to ballot outcomes.
Why Vitalik shifted: incentives, abuse, and practical experience
Vitalik's change of stance reflects a pragmatic recognition of evolving attack vectors. Public reasoning has highlighted two patterns:
- Targeted governance attacks — large token holders or hostile actors can publicly pressure known addresses, buy out noisy voters, or threaten legal/financial harm to sway votes. Privacy reduces this attack surface.
- Vote-buying and coercion economics — when wallets are visible, simple bribery or social pressure can flip decisions. Making the ballot secret increases the cost and complexity of buying votes.
In plain terms: the more observable and on-chain your stake is, the easier it is for adversaries to weaponize that observability. But that doesn't mean privacy is a panacea; it shifts the problem rather than erases it. Vitalik's public commentary and the two-layer blueprint aim to thread a middle path — preserve democratic expression while relying on economic prediction mechanisms to maintain accountability.
For further reading on the rationale and proposed architecture, see reporting that summarizes his position and the anonymous voting proposal.
The Tornado Cash-funded Ethereum DAO deposit: practical and regulatory trade-offs
When an Ethereum DAO accepted a deposit that reporting linked to Tornado Cash funds, it exposed an important, uncomfortable intersection between privacy tooling and compliance.
Tornado Cash (and TORN, the token commonly associated with some of its ecosystems) provides on-chain privacy by breaking the direct linkage between sender and receiver. That has legitimate privacy use-cases — from shielding dissidents to protecting financial privacy for individuals — but it has also attracted regulatory scrutiny because the same property can be used to launder funds. An article examining a DAO receiving Tornado Cash–sourced funds highlighted both the privacy implications and the optics of accepting such capital.
Practical trade-offs for a DAO that accepts Tornado Cash–derived funding include:
- Liquidity vs. reputational risk: The DAO gains immediate treasury resources, but it also inherits public scrutiny that can deter partners, custodians, and institutional counterparties.
- Regulatory exposure: Depending on jurisdiction, association with sanctioned or tainted privacy flows can trigger inquiries, asset freezes, or enforcement actions.
- Operational complexity: DAOs may need stronger AML/KYC policies on counterparties, or to segregate funds in a way that complicates treasury management.
From a governance perspective, the decision to accept such funds tests the ideals behind anonymous voting: if the wallet making the deposit is private or privacy-enhanced, how should membership, voting power, and influence be adjudicated? Should privacy-preserving contributions be accepted at face value, tokenized, or quarantined pending on-chain provenance analysis?
For a grounded examination of these events and their implications, see this reporting on the DAO deposit and Tornado Cash funding.
How anonymous voting can mitigate governance attacks — and its limits
Anonymous voting changes the attack surface in meaningful ways:
- It increases the friction for targeted coercion. Attackers cannot easily single out a voter’s address to threaten or bribe.
- It raises the cost of vote-buying. Buyers cannot easily verify that a purchased vote was cast as promised unless they collude to reveal a cryptographic proof, which introduces risk for both parties.
- It protects vulnerable participants (small holders, employees, or politically exposed people) from off-chain reprisals.
But anonymity brings its own limits and risks:
- Auditability gap: Secret ballots complicate post-hoc audits of vote integrity. Without careful design, it may be harder to prove an election was free from manipulation or collusion.
- Sybil and stake concentration: Anonymity does not solve the fundamental problem of stake-weighted voting. A single entity controlling many anonymous addresses still has outsized influence unless detection and anti-Sybil measures are added.
- Bribery via cryptographic receipts: Well-designed schemes can try to enable users to produce receipts proving how they voted; this undermines anonymity. Conversely, absolutely receipt-free voting may make vote-selling unverifiable but also makes accountability harder.
- Regulatory scrutiny: Anonymity can look like an attempt to evade compliance, inviting regulatory pushback or operational restrictions for the DAO and its service providers.
Anonymous voting reduces some attack vectors but does not eliminate the need for systemic checks: stake analysis, identity attestations (where appropriate), and economic incentives still play crucial roles.
Regulatory and compliance trade-offs to weigh
Compliance officers and DAO founders must evaluate the legal landscape. Key considerations:
- Jurisdictional variance: AML/KYC obligations and the legal treatment of privacy protocols differ widely. What is permissible in one jurisdiction can be prohibited in another.
- Counterparty risk: Service providers (exchanges, custodians, fiat on‑ramps) often impose their own restrictions based on regulatory perceptions; a DAO tied to privacy-layer flows may lose access to crucial services.
- Governance transparency vs. legal safety: Greater transparency helps satisfy auditors and regulators; privacy helps protect individuals. Finding a defensible middle ground is essential.
Practical steps to mitigate regulatory exposure include implementing clear provenance policies, maintaining records that allow compliance review without exposing individual votes, and designing treasury acceptance policies that specify when and how privacy-enhanced funds can be integrated.
Governance guardrails for DAOs considering privacy-enhancing tools
If a DAO is contemplating anonymous voting or accepting privacy-sourced funds, here are recommended guardrails to balance privacy, security, and compliance:
Define an explicit privacy policy: Publicly document why privacy is used, what it protects, and limits on usage. Transparency about intent reduces reputational ambiguity.
Layered voting architecture: Adopt the two-layer approach — private ballots for individual expression plus public prediction or indicator markets that signal aggregate belief and provide accountability.
Provenance checks for treasury inflows: Require a protocol for quarantining and investigating unfamiliar fund sources. Consider time-delays or escrow mechanisms before newly acquired funds are spendable.
On-chain and off-chain auditability: Use cryptographic proofs that preserve anonymity while enabling verifiable election integrity (for example, zero-knowledge proofs that show tally correctness without revealing votes).
Anti-Sybil and stake-smoothing measures: Combine stake-based voting with other signals (reputation, participation history, or delegated staking windows) to reduce the risk that an actor with disproportionate anonymous addresses controls outcomes.
Legal review and compliance liaison: Establish a standing legal review process and a compliance liaison who monitors regulatory guidance. Keep clear records that can be shared with auditors under confidentiality if needed.
Emergency governance pathways: Define emergency multisig or timelock mechanisms that can act if a governance process is suspected compromised — but ensure these mechanisms themselves are transparent and accountable.
Community education: Teach voters about vote-selling risks, privacy guarantees, and the role of prediction markets so that the community understands both the protections and limitations of the system.
Practical design patterns and examples
- Commit-reveal with ZK receipts: A commit-reveal voting with zero-knowledge proofs can allow private commitments off-chain with publicly verifiable tallies on-chain, reducing verification friction while maintaining voter privacy.
- Market-linked bonding: Require that proposers or large stakeholders post bonds whose slashing is tied to prediction-market outcomes to align incentives and deter malicious proposals.
- Graduated token utility: Newly received or privacy-enhanced funds can be tokenized as restricted-use units until provenance is confirmed, limiting immediate influence on governance.
These are not magic bullets — they are engineering compromises intended to align incentives, preserve privacy for legitimate users, and reduce both governance exploits and legal risk.
Conclusion: privacy is a tool, not a destination
Anonymous voting and privacy-preserving funding introduce powerful tools for protecting individuals and reducing certain governance attacks. But they also change the information environment: increasing the need for independent signals (like prediction markets), stronger provenance procedures, and legal hygiene.
DAO founders should treat privacy measures as one element of a broader governance stack. The two-layer model is promising because it acknowledges that privacy alone cannot ensure good outcomes; it must be paired with visible economic signals and institutional guardrails. Compliance officers should expect more questions from regulators and service providers, and proactively prepare provenance and audit plans.
As DAOs iterate, experimental deployments will teach us which designs scale in real-world adversarial and regulatory conditions. In practice, success will hinge on clear policies, thoughtful engineering, and ongoing dialogue between the technical community, governance researchers, and legal counsel. Bitlet.app and similar platforms that operate at the intersection of on‑chain payments and compliance will likely watch these developments closely as they influence treasury tooling and custodial practices.