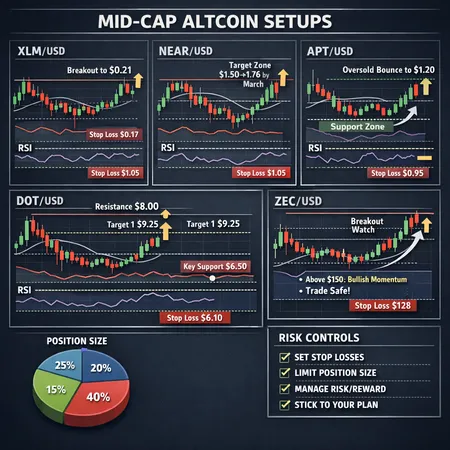
Why Vitalik Buterin’s Push on Zcash Privacy and L2s Matters for Protocol Design
Summary
Quick framing
Vitalik Buterin’s recent moves — a donation to Shielded Labs aimed at shoring up a Zcash crosslink/finality upgrade and a public clarification about the role of Layer‑2s in Ethereum’s wider ecosystem — matter because they blend practical engineering support with directional guidance. For protocol engineers and product leads tracking privacy upgrades, interoperability, and scaling, these are signals about priorities: privacy engineering should be robust, composable, and integrated into multi‑chain realities.
What the Shielded Labs donation signals for Zcash
On a surface level, the donation is financial support for a specific technical effort: Shielded Labs’ work to create a stronger finality or crosslink layer for Zcash. More concretely, backing a crosslink/finality design addresses a recurring problem in privacy coins — how to provide strong, auditable finality for shielded transactions without undermining privacy guarantees or relying on heavy trust assumptions.
A finality or crosslink layer for Zcash aims to do a few things at once: provide a single, canonical checkpointing mechanism that light clients and relays can rely on; enable better proofs of inclusion/exclusion for shielded states; and offer a safer substrate for interoperability (bridges, relays, and external auditors). The technical rationale for such a layer, and why it matters for cross‑chain security, is documented in recent coverage of the donation and the upgrade rationale (Blockonomi and Coinpedia).
For engineers: think of the crosslink as the minimal, verifiable source of truth that any interop primitive (relayer, zk proof verifier, Merkle‑light client) can reference. If implemented carefully, it reduces the attack surface for chain‑to‑chain messaging and can simplify privacy‑preserving light‑client designs.
Design tradeoffs to watch
- State vs. finality visibility: exposing too much finality metadata can leak timing or linking information about shielded transactions; keep checkpoint metadata compact and privacy‑preserving.
- Trust assumptions: does the crosslink rely on a committee, an external notary set, or economic finality? Each choice shifts the threat model.
- Proof costs: any crosslink mechanism should be mindful of proof generation/verification costs for ZEC wallets and relayers.
Those tradeoffs are why a targeted donation to Shielded Labs matters: this isn’t just funding; it’s endorsement of a direction that will require careful protocol work and broader ecosystem buy‑in.
Why an Ethereum founder supporting privacy work matters
When a prominent protocol founder signals support for privacy research or cross‑protocol upgrades, it does two important things: it legitimizes the work in the eyes of mainstream engineers and it nudges resources (contributors, auditors, tooling) toward shared public goods. Vitalik’s donation is not an isolated plea for privacy — it’s a signal that privacy engineering is compatible with long‑term interoperability and robust finality.
Practically, this can catalyze: more auditors who previously focused on smart contracts to look at Zcash primitives; cross‑pollination between Zcash’s shielded‑proof expertise and Ethereum’s growing zk stack; and wallet/infrastructure vendors to prioritize ZEC support alongside ETH. For protocol design, the message is clear: privacy features shouldn’t be exotic or siloed — they need to be engineered with the same rigor as consensus and finality layers.
This shift is relevant to markets as well: improving crosslink security reduces bridge risk and may change how custodians and OTC desks view ZEC liquidity and custody. It’s also a subtle change in narrative—privacy is not anti‑composability. Done right, it enhances the broader composable ecosystem rather than obstructing it.
Vitalik’s L2 clarifications and what they reshape
Vitalik’s recent public clarifications about L2s reframed expectations: rather than a single universal solution to scaling, the ecosystem should expect a diverse set of Layer‑2 approaches to coexist and interoperate. His comments emphasize that L2s are an evolving design space with different tradeoffs — optimistic rollups, zk rollups, plasma variants, and specialized finality layers each have roles. See his broader remarks summarized in coverage like ZyCrypto’s article on L2 role clarifications (ZyCrypto).
For product and protocol architects, the practical takeaway is: design with interoperability and composability in mind. Expect cross‑L2 messaging, canonical finality anchors, and standardized proof formats to matter more than choosing one rollup “winner.” That expectation dovetails with the Zcash crosslink idea — both are about establishing verifiable anchors that different systems can trust without sacrificing their internal invariants.
Interoperability primitives that gain importance
- Portable finality proofs (compact, non‑leaking) that can be validated across chains.
- Standardized light‑client interfaces for shielded states.
- Composable proof formats that allow zk proofs for privacy to be embedded in L2 proof streams.
By clarifying these expectations, Vitalik reduces the political friction around heterogeneous designs and implicitly encourages engineering that prioritizes clean interfaces over monolithic implementations.
Potential impacts on ZEC, ETH coordination, and privacy tooling adoption
Short term: the donation and L2 messaging create momentum. ZEC gains increased attention from auditors, devs, and integrators; ETH developers become more open to integrating privacy primitives into rollup or finality tooling; and tooling vendors (wallets, relayers, bridges) have stronger incentives to support shielded workflows.
Medium term: expect better infra—improved light clients, shared test suites for crosslink verification, and possibly reference implementations of privacy‑friendly finality proofs. That reduces integration friction for bridges and custodial services and could modestly increase on‑chain and off‑chain demand for ZEC as a privacy rail.
Longer term: we could see more formal collaboration between Zcash teams and Ethereum L2 teams around shared proof standards or crosslink semantics. For example, an ETH rollup might accept a ZEC finality anchor as part of a dispute or exit protocol, or a bridge could rely on a Zcash crosslink to verify shielded state transitions without off‑chain oracles.
Effects on token and market dynamics
- ZEC: better security and easier tooling could reduce custody/bridge risk premiums; adoption in privacy‑sensitive rail use cases could increase. But markets also price in execution risk: the upgrade must be implemented and audited.
- ETH: clarifying L2 expectations helps ecosystems allocate engineering resources more predictably; it may accelerate rollup with privacy integrations (e.g., rollups that can verify shielded proofs), indirectly benefiting ETH utility.
Implementation considerations and risks
Engineers and product leads should treat this period as an opportunity to define interoperable interfaces carefully. A few practical points:
- Define compact crosslink proof schemas that minimize metadata leakage.
- Build shared test vectors and adversarial scenarios for cross‑chain proof verification.
- Consider hybrid economic finality designs that combine cryptoeconomic challenge windows with compact checkpointing to limit trust while preserving privacy.
- Maintain rigorous auditing cycles: privacy primitives are subtle and regular audits are non‑optional.
There are risks: rushed interoperability can introduce subtle privacy leaks; integrating finality anchors incorrectly can swap one trust assumption for another; and economic incentives for validators or relayers need to align with privacy goals.
What product leads should do next
- Track Shielded Labs’ implementation roadmap and audit plans; align integration windows for wallets and relayers.
- Push for standardized proof formats and light‑client APIs across ETH and ZEC toolchains.
- Evaluate whether existing L2 or bridge designs can accept privacy‑preserving proof inputs without weakening their security models.
- Coordinate with auditor teams early: include privacy adversaries and trace‑analysis scenarios in threat modeling.
Teams building on Bitlet.app or similar platforms should add ZEC support planning into their privacy feature roadmaps now, where appropriate, and stay tuned for cross‑protocol testnets.
Closing thoughts
Vitalik’s dual moves — supporting Shielded Labs’ crosslink work and clarifying L2 roles — are best read together. They point to a future where privacy engineering, finality anchors, and diversified scaling approaches are complementary pieces of a more interconnected multi‑chain stack. For protocol engineers and product leads, that future means more coordination but also clearer incentives to build modular, interoperable, and privacy‑aware primitives.
If your team is designing an L2, a bridge, or a wallet, treat this as a prompt: prioritize compact, auditable crosslink proofs and standard interfaces now rather than retrofitting privacy later. The engineering choices you make will determine whether privacy becomes a first‑class property across chains or remains a niche add‑on.
Sources
- Vitalik Buterin backs Zcash upgrade (Shielded Labs)
- Blockonomi coverage on donation and crosslink security rationale
- Vitalik’s clarifications on the role of L2s
(For context on market bellwethers and broader DeFi sensitivity to finality, many engineers also watch how Bitcoin and DeFi ecosystems react to cross‑chain finality improvements.)