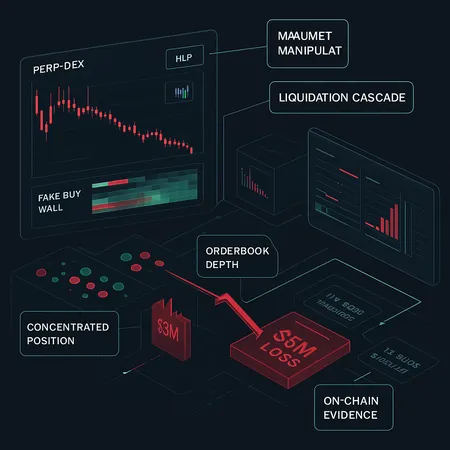
How a $3M Sacrifice Triggered a $5M Perp Crash: Hyperliquid, HLP Exposure and the POPCAT Fallout
Summary
Executive summary
Late-stage analysis of the Hyperliquid incident suggests an attacker accepted a roughly $3M deliberate loss to change market dynamics — ultimately triggering cascading liquidations and approximately $5M in downstream losses. The collateral damage extended to POPCAT, which saw a sharp price collapse and manipulation allegations. What looks like a straightforward perp market move is better understood as a coordinated exploit that combines perpetuals mechanics, fake depth, and centralized HLP exposure.
This report is written for experienced DeFi traders and risk teams. It reconstructs the plausible attack flow, shows the on-chain signals that betray coordination, explains why AMM-perp designs and concentrated HLPs amplify contagion, and lists practical mitigations at both trader and protocol levels. Mention of Bitlet.app appears where relevant to operational tooling and alerts.
How perp-DEX mechanics amplify a targeted attack
Two design primitives common to modern decentralized perpetuals exchanges explain why a relatively small, purposeful sacrifice can cascade into outsized losses.
1) AMM-based mark price coupling and limited liquidity
Many perp DEXs use an internal pricing mechanism (vAMM, virtual AMM, or liquidity pool) to derive the mark price. The mark is sensitive to order size relative to available liquidity. Large taker trades move the mark quickly; with thin depth, a sequence of aggressive trades can shift the mark far enough to push cross-margined positions into undercollateralization.
If an attacker is willing to absorb immediate slippage (the ~$3M sacrifice), they can move mark and trigger nearby liquidations. With on-chain, transparent pools it’s trivial to calculate how much slippage is needed to reach a liquidation threshold.
2) HLP (Hyperliquid Pool) as an absorptive but concentrated liquidity backstop
The HLP is designed to backstop the AMM and provide deep liquidity; however, if the HLP itself holds concentrated residual risk (large positions, a small number of LPs, or significant single-token exposure), losses realized by the pool are socialized or cause cascading withdrawals. The HLP therefore becomes a fragile shock absorber: instead of smoothing volatility, it can amplify contagion when its utilization or share concentration is high.
3) Funding, open interest and liquidation engine behavior
Perp funding and open interest add second-order effects. A manipulated mark can invert funding flow, incentivizing traders in one direction and increasing the effective leverage of leveraged shorts/longs. Liquidation engines that execute as large market orders against the same AMM can worsen slippage and create a feedback loop.
Anatomy of the Hyperliquid / POPCAT sequence (reconstructed)
This reconstruction uses common on-chain forensic techniques: looking at order/trade sequences, funding rate moves, HLP deposit/withdraw events, and wallet clustering. The exact txs are public; investigators should trace the sequences below using event logs.
Step 1 — Pre-positioning and concentration
- Large accounts accumulate directional exposure in HYPE/POPCAT perpetuals. These may be concentrated in a handful of wallets or routed through known trading bots.
- HLP composition shows significant token exposure or asymmetric hedges. Large LPs may not immediately exit due to lockups or incentive schedules.
Step 2 — Creating a false depth signal (spoofing / fake buy walls)
- The attacker posts visible buy-side depth that looks legitimate. On-chain DEX order books or visible limit orders are spoofed by placing and rapidly canceling orders or by creating chained positions that mimic market-making.
- Concurrent off-chain activity (private orders on CLOBs, OTC, or coordinated wash trading) can further distort perceived liquidity.
Step 3 — The sacrificial taker trade
- The attacker executes a large taker trade that incurs heavy slippage and immediate P&L loss (the reported ~$3M). That trade forces the mark price across the vAMM in a direction that makes many leveraged positions undercollateralized.
- Because liquidation execution often uses the same pool, the liquidator market orders create additional adverse movement.
Step 4 — Liquidation cascade and HLP losses
- Liquidations hit concentrated accounts or cross-margined positions. If liquidator flows are large relative to pool depth, auto-liquidations cascade.
- HLP absorbs the residual loss. If HLP share concentration is high, a few LPs take outsized hit; if socialized losses or protocol-level underwriting occur, the broader pool value drops and more positions are threatened—creating a contagion loop.
Step 5 — Price and narrative contagion (POPCAT crash)
- A sudden on-chain price collapse prompts off-chain liquidity providers and CEXes to update risk parameters, which can lead to orderbook withdrawals and market panic. Social media and on-chain front-runners amplify the move, turning a tactical attack into a market story and further liquidity evaporation.
On-chain evidence and heuristics to detect coordination
Below are practical signs you can search for on-chain. These are not proof in isolation but useful heuristics:
- Large single trades moving the vAMM mark followed immediately by liquidations on the same asset. Correlate trade timestamps and liquidation events.
- Wallet clustering: the same or related clusters post both the depth-making orders and the sacrificial taker trade.
- Rapid order cancellations and re-posting tendencies around the time of the event (high cancel-to-fill ratio indicates spoofing).
- Synchronous HLP outflows or internal accounting events (mint/burn, fee extractions) that align with the time window of the attack.
- Funding rate spikes or abrupt reversals immediately after the marker trade — indicating changed incentives and new stress on cross-margin positions.
- Open Interest (OI) mismatch: a large movement in OI without commensurate off-chain hedging suggests synthetic buildup.
To investigate, download event logs for OpenPosition, Liquidation, Deposit, Withdraw, and Transfer for the HLP contract and perp markets. Reconstruct the position ledger by replaying events to identify who made and absorbed losses.
Why current exchange-level controls often fail
Several commonly-suggested controls are present on many protocols but fail under coordinated attacks:
- Static liquidation multipliers: when markets move fast, a fixed liquidation size executed as a single order will produce catastrophic slippage.
- Thinly parameterized insurance funds: funds sized for historical volatility, not for engineered attacks, are drained quickly.
- Single-oracle dependence: reliance on one price feed enables mark manipulation if the oracle is short-windowed or easily gamed.
- No concentration limits: a handful of LPs can collectively bear outsized HLP risk without protocol checks.
Practical mitigations for protocol designers
Design choices can materially reduce both the probability and impact of these attacks. Key recommendations:
Governance and parameterization
- Enforce position and HLP exposure limits: max position per wallet, max single-LP share, and utilization caps. Require staggered withdrawals for large LPs.
- Dynamic margining: margins and allowed leverage should increase as utilization, funding skew, or bid-ask depth deteriorate.
Liquidation architecture
- Throttle liquidation execution: break large liquidations into TWAP-style executions or staggered auctions to avoid single-order slippage spikes.
- Prioritize on-chain auctions for large positions with off-chain executors under strict slippage caps; auction winners post bonds to discourage front-running.
Oracles and price aggregation
- Use time-weighted median oracles with multi-source aggregation and outlier rejection windows long enough to blunt single-trade mark gyrations.
- Add a circuit breaker that pauses mark updates to the perp engine if oracle-price vs. vAMM diverges beyond a configurable threshold for a short time.
HLP design
- Diversify HLP risk: require multi-asset, multi-provider HLP composition with enforced hedges or index-based collateralization.
- Implement loss-sharing caps and dynamic fee allocation toward insurance funds when utilization spikes.
- Monitor LP concentration and require governance action or temporary caps when a single entity exceeds a threshold.
Monitoring, alerts and on-chain transparency
- Provide real-time dashboards for HLP utilization, big wallet changes, funding rate anomalies, and orderbook depth. Integrate alerts for the signals mentioned in the previous section.
- Store and publish liquidation execution traces to help post-incident audits.
Practical mitigations for traders and risk teams
Even with excellent protocol controls, traders must manage residual risk. Recommended tactics:
- Limit leverage on thin markets: reduce leverage when funding skew, OI growth, or HLP utilization increases.
- Pre-define liquidation risk: compute required adverse mark moves to trigger your liquidation and size positions so that available liquidity is sufficient to absorb that shock.
- Monitor HLP health: track HLP TVL, concentration, and recent P&L; if HLP draws down rapidly, reduce exposure or unwind positions carefully.
- Use limit/twap exits and native exchange risk features: avoid all-in market orders during stress windows. If you're at risk, prefer staggered exits to force liquidators to pay longer slippage.
- Keep an eye on funding rates and base your trade horizon on funding expectations; sudden funding reversals are a red flag.
- Off-chain tools and alerting: tie trading to on-chain alert systems (DEX event monitors, wallet trackers, funding monitors). Bitlet.app and similar tools can be integrated into a risk stack for real-time signals.
Post-incident playbook for protocol teams
When an attack occurs, quick triage and transparent communication matter as much as technical fixes:
- Immediate response: pause new positions if mark/oracle divergence is extreme; throttle large withdrawals from HLP temporarily.
- Audit and publish a timeline: release an on-chain timeline of trades, liquidations, and HLP moves for community scrutiny.
- Rebuild trust through concrete steps: inject protocol risk capital if governance decides, resize insurance funds, or temporarily limit leverage until parametric fixes are in place.
Final thoughts — design for adversarial markets
DeFi markets are adversarial by design: every visible incentive can be gamed. The Hyperliquid/POPCAT episode is a textbook example of how market manipulation + perp mechanics + concentrated HLP exposure produces outsized systemic losses. Protocol designers must accept that traditional market assumptions (passive LPs, deep continuous liquidity) do not always hold in a permissionless environment.
For traders and risk teams the lesson is simple but hard: assume that any observable liquidity can be weaponized. Combine position limits, active monitoring, and conservative leverage to survive engineered shocks.
This post aimed to provide a technical post-mortem and prescriptive mitigations. For teams wanting operational tooling and alert integrations, consider integrating on-chain monitors and execution-safe tooling into your stack — tools like Bitlet.app and custom alert workflows can be part of a resilient approach.
If you want a follow-up, I can provide a checklist for on-chain forensic queries (event logs, heuristic SQL queries for common DEX schemas) and sample liquidation throttling algorithms to implement in a perp engine.