Quantum Computing and Bitcoin: When to Prepare, What to Do, and Why Panic Is Premature
Summary
Executive summary
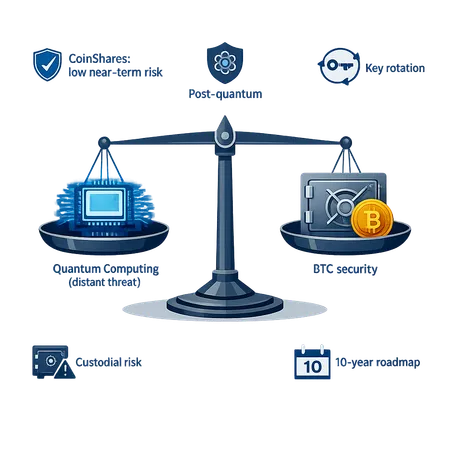
Quantum computing headlines are noisy. For institutional portfolio managers and custody teams managing BTC, the real question is when and how to act — not whether to panic. CoinShares’ recent take, summarized by outlets like DailyHodl and BeInCrypto, frames the threat as distant and manageable; this piece lays out the technical reasons why, practical mitigation pathways (key rotation, post-quantum cryptography, custodial changes), and an operational checklist for custody teams.
What “quantum risk” actually means for Bitcoin
At a high level, the quantum concern for Bitcoin is simple: most of Bitcoin’s cryptography (ECDSA and Schnorr) depends on the hardness of the discrete logarithm problem over elliptic curves. A large, fault-tolerant quantum computer running Shor’s algorithm could, in theory, recover private keys from public keys, enabling signatures to be forged and funds stolen.
Two important qualifiers cut the immediate danger considerably:
- Hardware scale and error correction: Implementing Shor on cryptographically relevant curves requires not just dozens but millions of physical qubits plus error correction and very low logical error rates. That hardware is not on the near-term roadmap for most research programs.
- Limited attack surface on Bitcoin: Many BTC outputs do not expose the public key until the owner spends them; addresses that use hashed public keys (legacy P2PKH, P2WPKH) reduce the window where a quantum adversary can work with the public key directly. Even when a public key does appear on-chain, an attacker still needs time and a huge quantum computer to turn that into a private key.
These points are why analysts such as CoinShares judge the risk as distant and manageable. For their public briefing and reporting see DailyHodl and BeInCrypto covering CoinShares’ view.
Why current Bitcoin keys are safe for now — technical details
A few concrete technical defenses exist today that substantially slow any quantum attack against BTC holdings:
Address hashing reduces exposure: Most common address types (P2PKH, P2WPKH) store the hash of a public key on-chain. The actual public key becomes visible only when the output is spent. If a user never reuses an address, an attacker cannot retroactively derive a private key from a hidden public key in the UTXO set.
Spending windows are short for hot wallets: Hot-wallet private keys are often used briefly and then rotated or moved to cold storage. An adversary would need to act in a small window of time around a spend to exploit a revealed public key.
Taproot nuance: The Taproot upgrade (Schnorr signatures) improves privacy and contract flexibility, but it also means many Taproot outputs include a public-key-like construct in the output. That changes the exposure calculus: Taproot users still gain privacy and efficiency, but custodians should be aware Taproot outputs can make the public-key surface visible earlier than hashed-address types. The practical implication is not immediate doom, but a reason to incorporate Taproot-aware key policies into a migration plan.
No known short-cuts: There is no currently-known classical or near-term quantum shortcut that turns typical UTXO data into usable private keys on affordable hardware. In short: Bitcoin’s cryptographic plumbing imposes real friction on any would-be quantum attacker.
CoinShares’ position: measured and actionable
CoinShares — summarized in reporting by DailyHodl and BeInCrypto — argues quantum risks are tractable and not imminent. Their reasoning rests on three pillars:
- Hardware timelines: Large, error-corrected quantum computers capable of breaking widely used elliptic curves are still years (likely a decade or more) away, per current engineering roadmaps.
- Mitigation is available: We already have well-researched post-quantum algorithms (NIST’s selections like CRYSTALS-Kyber/CRYSTALS-Dilithium) and operational mitigations such as key rotation and cryptographic agility that can be implemented ahead of time.
- Risk management beats panic: Given the long lead time, institutions can plan upgrades and deploy mixed-scheme defenses (classical + post-quantum) without disrupting custody operations.
CoinShares’ view is not denialism — it’s risk prioritization: monitor hardware milestones, prepare migration paths, and avoid emergency, wholesale changes that would introduce operational risk.
Practical mitigation pathways over the next decade
Below are operational paths custody teams can adopt now. These are ordered from easiest/lowest friction to more structural changes that require coordination with the wider Bitcoin ecosystem.
1) Immediate controls and key hygiene (months)
- Enforce no address reuse as a hard policy for all custody wallets; rotate keys on every outbound settlement where practical. Use deterministic wallets that make rotations auditable.
- Segregate long-term cold holdings from operational hot funds. Only retain minimal online balances for settlement.
- Maintain a live inventory of script types and address exposure (identify how much BTC sits in P2TR vs P2WPKH/P2SH).
- Update SLAs and threat models to track quantum milestones reported by major labs.
2) Key rotation and sweeping strategies (6–24 months)
- Define a rotation policy for custodial keys: e.g., sweep non-critical balances to newly generated keys every N years, and rotate keys after any critical software or stack change.
- For large legacy holdings, consider planned batched sweeps during low-fee windows to reduce cumulative exposure. Sweeping moves funds from older key types into new addresses under stricter policy.
- For Taproot-heavy holdings, adopt a policy where long-term cold storage uses address types that minimize early public-key exposure when possible.
3) Custodial architecture and threshold approaches (1–3 years)
- Accelerate deployment of Multi-Party Computation (MPC) and threshold-signature schemes. These reduce the value of stealing a single key: an attacker must compromise multiple parties.
- Implement mixed-signature thresholds that require both classical ECDSA/Schnorr shares and an additional post-quantum signature or factor. This increases transition flexibility.
- Re-evaluate third-party custody contracts: demand transparency on key rotation plans and PQC roadmaps from sub-custodians.
4) Post-quantum cryptography pilots and integration (2–7 years)
- Start cryptographic agility trials off-chain (wallet software, APIs, L2 solutions). Pilot PQC algorithms that NIST has standardized (e.g., Kyber for KEM, Dilithium-like schemes for signatures) in isolated testnets and custodial signing stacks.
- Explore hybrid signatures: signatures that combine classical ECDSA/Schnorr and a PQC signature. Hybrids protect funds during the migration window.
- Plan for a future Bitcoin soft-fork or higher-layer migration path for native PQC support; this is a long lead-time political and engineering effort and requires community coordination.
Custodial risk: what to ask vendors and regulators now
Institutions should treat quantum risk like other systemic tech risks: document exposure, quantify it, and require evidence of mitigation.
Key questions to custodians and vendors:
- What is your key rotation cadence and how do you prevent address reuse?
- Do you maintain an inventory of address types and their public-key exposure (P2TR vs P2WPKH vs P2PKH)?
- Are you piloting MPC or hybrid-signature schemes, and can you provide timelines for production-ready PQC adoption?
- How would you execute an emergency mass-sweep if a credible quantum breakthrough occurred? Is there a tested playbook?
Regulators and compliance teams will expect documented policies. Bitlet.app and custody providers will need to show the same level of preparedness.
Timelines, monitoring, and decision triggers
A pragmatic institutional plan uses decision triggers that map quantum milestones to actions, for example:
- Trigger A (3–7 years): Public demonstration of a fault-tolerant quantum computer with thousands of logical qubits — begin immediate acceleration of PQC pilots and prioritize sweeping of the most-exposed funds.
- Trigger B (1–3 years after A): Multiple independent demonstrations and a published attack blueprint — move to hybrid signatures and increase rotation cadence for any address types that reveal public keys.
- Trigger C (shortened window): If a near-term demonstration shows feasibility of practical key recovery in operational timeframes, execute emergency migrations per a pre-tested plan.
Monitor sources from quantum hardware labs, academic literature, and the crypto industry. CoinShares’ analysis is useful as one input, but do not make it the only one.
Why sensational coverage is misleading (and potentially harmful)
High-profile media pieces that predict a total collapse of Bitcoin can be persuasive — but they often omit key context:
- They rarely quantify the hardware and error-correction gap between today's machines and the ones required to break Bitcoin’s curves.
- They ignore existing mitigations such as address hashing, key rotation, and wallet-level defenses.
- Sensational framing can produce rushed, brittle responses (e.g., mass code changes or unsafe migrations) that introduce more operational risk than measured transition plans.
For an example of sensational coverage that drew strong reactions from parts of the community, see the Financial Times story and the subsequent critique covered by CoinTribune, which framed extreme outcomes without the technical caveats. Linking such pieces against measured technical analyses like CoinShares’ reporting shows why measured planning beats panic: CoinTribune/FT critique.
Practical checklist for portfolio managers and custody teams
- Inventory: Identify total BTC exposure by address type and likelihood of public-key exposure. Prioritize high-value UTXOs for mitigation.
- Policy: Enforce address non-reuse, document rotation cadence, and mandate cold/hot segregation.
- Vendor diligence: Require custodians and wallet vendors to publish PQC roadmaps and MPC adoption timelines.
- Pilots: Run PQC signature and hybrid-signature pilots in test environments; evaluate performance and signature sizes vs network fees.
- Playbook: Build and test emergency sweeping and rotating playbooks; rehearse them periodically.
- Monitoring: Subscribe to quantum hardware milestone trackers and integrate decision triggers into governance.
Bottom line for institutional teams
Quantum computing is a real, long-term cryptographic threat — but not an immediate one. CoinShares’ position (as reported by outlets like DailyHodl and BeInCrypto) is that the threat is distant and manageable if institutions follow a structured plan: tighten key hygiene now, pilot PQC and threshold cryptography, and maintain clear decision triggers tied to hardware milestones. Sensational headlines that predict sudden collapse miss both the technical realities and the range of mitigation options available to custody teams.
Planning, not panic, is the rational posture: inventory exposure, rotate keys, pilot post-quantum options, and require transparency from custody vendors. That approach protects assets today while buying time to migrate cleanly when PQC readiness and community consensus are in place.
Sources
- CoinShares coverage summarized by DailyHodl: "Bitcoin's quantum risks remain distant according to CoinShares — here's why" — https://dailyhodl.com/2026/02/09/bitcoins-quantum-risks-remain-distant-according-to-coinshares-heres-why/
- BeInCrypto on CoinShares’ position: "Bitcoin quantum computing risk manageable, CoinShares says" — https://beincrypto.com/bitcoin-quantum-computing-risk-manageable-coinshares/
- Example of sensational coverage and critique: CoinTribune on the FT piece — https://www.cointribune.com/en/the-financial-times-under-fire-after-its-radical-view-on-the-total-collapse-of-bitcoin/?utm_source=snapi
For deeper technical background on post-quantum primitives, review NIST’s selections and ongoing literature on hybrid-signature deployments. For custody teams building migration plans, consider consulting with cryptographers and wallet engineers and tracking both hardware milestones and community governance discussions related to protocol-level changes.
(Internal note: for Bitcoin-specific operational guidance and wallet tooling, see resources under Bitcoin and broader ecosystem implications in DeFi.)