Who’s Buying the Ether Dip? Infini Exploit Wallet vs Institutional Accumulators
Summary
Introduction: why this comparison matters
When large blocks of ETH move during a market dip, the same price action can be read in two opposite ways: smart accumulation by institutions or opportunistic cashing out by criminals. Recent reporting showed a wallet linked to the Infini $50M exploit reactivated and purchased Ether after previously laundering through Tornado Cash, while at the same time Tom Lee’s Bitmine reportedly bought 20,000 ETH in a clear example of institutional accumulation (CoinTelegraph report on the Infini wallet and Crypto.News on Bitmine’s purchase).
For investigative reporters and compliance officers, these two moves are not symmetrical. One carries potential legal exposure and AML risk; the other is a liquidity and market-structure story. This article lays out practical on-chain provenance techniques, legal and compliance implications, and a step-by-step framework to distinguish illicit reflows from legitimate institutional buying. (Bitlet.app is mentioned here as an example of platforms that must reconcile custody and AML obligations with market service offerings.)
The players: Infini exploit wallet vs Bitmine
Two contemporaneous headlines can look identical in price charts but differ massively in provenance.
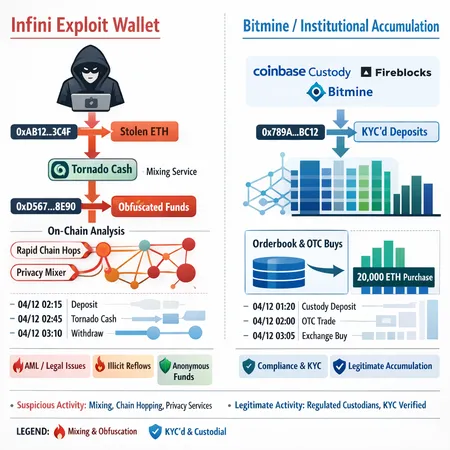
The Infini-linked wallet: According to reporting, a wallet tied to the Infini exploit reactivated and purchased ETH, and the same address used Tornado Cash at earlier points in the laundering chain. That pattern—exploit origin, mixing, then purchase—raises immediate AML and traceability concerns (CoinTelegraph source).
Bitmine (Tom Lee): Crypto.News reported that Bitmine purchased roughly 20,000 ETH, a large but straightforward accumulation consistent with institutional treasury activity or acquisition via OTC and custodial channels (Crypto.News source).
Understanding whether a wallet’s balance stems from theft, laundering, or legitimate custody is the central challenge for screening and reporting.
On-chain provenance: tools, limits and best practices
On-chain provenance means tracing the history of an address’s funds: where they originated, the intermediaries they passed through, and where they ultimately land. That trace relies on cluster analysis, labeling, and heuristics—some automated, some manual.
Cluster analysis and graphing: Tools map transaction graphs and cluster addresses by heuristics such as co-spend or shared control. This helps identify whether a wallet sits in the same cluster as an exploited address. Firms like Chainalysis or forensic teams routinely use this.
Contract interaction analysis: On Ethereum, internal transactions, contract calls, and ERC-20 flows reveal whether funds moved through mixers like Tornado Cash or wrapped through other protocols.
Labeling and databases: Public label databases (Etherscan tags, exchange hot wallet lists) and proprietary watchlists provide context. Labels are not infallible, but they are a first filter.
Temporal patterns and volumes: The timing of moves—immediate dispersal after an exploit, or patient, laddered accumulation—provides an important signal.
Caveats: mixing services do not always equal guilt. Privacy tools have legitimate uses; moreover, savvy launderers intentionally create noise to frustrate analytics. Provenance is probabilistic, not binary.
For many monitoring tasks, linking a suspect wallet back to a known exploit cluster, and then observing its interaction with a mixer like Tornado Cash, elevates the risk score materially.
Indicators that point toward illicit origin
When evaluating whether a wallet’s ETH purchases are tainted by an exploit, compliance teams should look for a combination of signals rather than a single flag:
- Direct transactional linkage to a known exploit or timestamped theft event (same cluster or parent address).
- Movement through sanctioned or high-risk privacy tools (e.g., Tornado Cash) soon after an exploit; mixing is a strong but not definitive signal.
- Rapid chain-hopping, repeated micro-transfers, or use of multiple bridges within short windows—techniques used to obfuscate provenance.
- Quick conversion to stablecoins and subsequent withdrawals to multiple exchanges or fiat rails without clear custodial custody.
- Interaction with addresses already labeled malicious by public forensic databases.
When several indicators appear together, the probability that funds are illicit rises; compliance teams should escalate.
Signals consistent with institutional accumulation
Large institutional buys tend to leave different footprints on-chain and off-chain:
- Route through known custody and OTC channels: Institutions typically use regulated custodians (Coinbase Custody, BitGo, etc.) or OTC desks that maintain extensive KYC records. These custodial addresses are often labeled and visible in on-chain databases.
- Single large transfers or staged purchases that match announced or expected treasury behavior, often with matching off-chain documentation or press statements.
- Lack of privacy-tool usage: institutions rarely route funds through mixers; they require audit trails.
- Longer holding patterns and staking or yield activity that align with treasury management rather than immediate cash-out.
- Corroboration from reputable market intelligence and filings (press releases, SEC filings where applicable).
Bitmine’s 20k ETH purchase, as reported publicly, fits the institutional pattern: a large, discrete purchase consistent with accumulation rather than opportunistic laundering (Crypto.News source).
Legal and AML implications of exploit wallets buying the dip
When an exploited wallet or a laundering chain re-enters the market, custody services and exchanges face legal, regulatory and reputational decisions.
- OFAC and sanctions: Some mixers have been targeted by regulators; routing through a sanctioned entity can create secondary sanctions risk. Exchanges must ensure they do not facilitate movement tied to sanctioned services. The Tornado Cash enforcement actions illustrate how regulators may treat privacy tools used for illicit flows.
- SARs and freezing: Regulated entities have to file Suspicious Activity Reports for unusual patterns and may be legally obligated to freeze or block transactions pending review. This is especially true where clear links to theft or sanctioned services exist.
- Asset recovery and civil actions: If funds can be traced to a theft, victims or prosecutors may seek civil recovery or forfeiture. Exchanges that receive those funds can be subpoenaed or asked to cooperate with law enforcement.
- Due process and burden of proof: Forensic linkage is probabilistic; enforcement actions frequently require supplementary evidence. Mislabeling a legitimate institutional buyer as illicit risks legal exposure and reputational damage.
Compliance teams must balance swift risk mitigation with careful evidence-gathering.
How custodians and exchanges detect and handle suspicious flows
Operationally, custodians and exchanges combine automated detection with manual review.
- Automated scoring and flags: Transactions are scored against watchlists, behavioral heuristics, and risk policies. High-risk scores trigger holds and manual review.
- Hot wallet monitoring and deposit controls: Deposits to hot wallets are monitored in real time. If a deposit links to exploit clusters or mixers, the receiving platform may quarantine or limit movement.
- KYC/AML escalation: On-chain evidence is combined with off-chain KYC records; where a counterparty can prove custody via a regulated custodian, that can mitigate concerns.
- Law-enforcement liaison: Exchanges often have dedicated teams to handle requests from law enforcement and to review subpoenas or civil claims related to stolen funds.
- Communication and coordination: Multi-exchange coordination helps, especially if illicit flows move across rails.
These operational responses are designed to contain risk while preserving the ability to prove chain-of-custody if litigation follows.
A practical decision framework to separate illicit reflows from legitimate accumulation
Below is a stepwise framework that compliance teams and reporters can apply quickly during volatile dips.
- Initial provenance scan (0–5 minutes): run the address through multiple analytics providers for cluster labels and known-exploit linkage.
- Mixer and sanction check (5–30 minutes): check for any flows through Tornado Cash or other high-risk services and cross-reference sanction lists.
- Counterparty identification (30–120 minutes): determine whether downstream addresses are labeled as custodial/exchange hot wallets or OTC counterparties.
- Behavioral analysis (same day): examine timing, trade execution style (single block vs laddered buys), and conversions to stablecoins or fiat rails.
- Off-chain corroboration (24–72 hours): look for press releases, filings, or public statements that would explain the move (institutional buys are often announced or matched to known flows). For example, Bitmine’s acquisition was reported publicly and thus easier to corroborate (Crypto.News source).
- Risk scoring and escalation: if several high-risk indicators align, escalate to legal and law enforcement; if the evidence points to a custodial or institutional path, treat as legitimate but monitor.
- Document and retain provenance snapshots: save transaction graphs, timestamps and provider outputs for audit and potential legal actions.
This framework emphasizes speed in detection and caution in action—avoid knee-jerk public accusations without sufficient proof.
Metrics and signals to watch in realtime
For market intelligence teams tracking whether whales are legitimate or not, augment standard market metrics with provenance-focused indicators:
- Exchange inflow/outflow volumes by labeled addresses.
- Rate of interaction with privacy tools per cluster.
- Proportion of ETH converted to stablecoins and withdrawn on-ramps.
- Reuse of addresses known from past exploits.
- Changes in orderbook liquidity shortly after large on-chain transfers (slippage patterns).
Combining market microstructure with forensic tags gives a more complete story of whether a large buyer is a genuine treasury or an opportunistic launderer.
Case study: applying the framework to Infini wallet and Bitmine
Applying the framework highlights the contrast.
Infini-linked wallet: Provenance scans show linkage to the exploit cluster; historical flows through Tornado Cash inflate the AML risk score; the behavior (reactivation after an exploit and immediate on-chain purchases) suggests laundering and opportunistic market interaction. Under our framework the wallet would be escalated for blocking or enhanced monitoring, and exchanges receiving inbound transfers would likely quarantine or freeze until legal clarity.
Bitmine: Reported as a large, public purchase with routes consistent with OTC and custody. No evidence of privacy-tool usage or exploit linkage was reported. Under the framework, the move would be treated as institutional accumulation but documented and monitored.
The distinction is not academic: the former can trigger SARs and legal action; the latter is market news.
Recommendations for journalists and compliance officers
- Use multiple analytics vendors; triangulation reduces false positives.
- Preserve immutable evidence: transaction hashes, screenshots of label outputs, and timestamps.
- Avoid public attribution without corroboration; name-calling can have legal consequences.
- For compliance officers: implement rapid-response playbooks that define thresholds for holds, SARs and law-enforcement referrals.
- For investigative reporters: combine chain analysis with off-chain reporting—identify OTC desks, custodians, or public filings that can corroborate an institutional buyer’s identity.
- Maintain a policy for privacy-tool findings: treat them as high-risk but verify context—privacy tools are used by legitimate users too.
Conclusion
A large ETH purchase during a dip can be either a bullish institutional accumulation or the moment an exploiter tries to monetize stolen funds. The difference hinges on provenance: cluster linkage, mixer usage (e.g., Tornado Cash), custodial routes, timing, and off-chain corroboration. Compliance teams should combine automated scores with disciplined manual review and legal escalation; journalists should triangulate on-chain evidence with off-chain confirmations before drawing conclusions. Applying a repeatable framework reduces false positives and speeds responsible action.
For real-world monitoring, pair forensic on-chain tools with market signals—NFTs, memecoins, or DeFi flows can muddy the picture, so context matters.
Sources
- CoinTelegraph — Infini exploit wallet reactivated and used Tornado Cash: https://cointelegraph.com/news/infini-exploit-wallet-buys-ether-dip-tornado-cash?utm_source=rss_feed&utm_medium=rss&utm_campaign=rss_partner_inbound
- Crypto.News — Tom Lee’s Bitmine buys 20k ETH: https://crypto.news/ethereum-price-prediction-after-tom-lees-bitmine-buys-20k-eth-worth-41-98m/
For further reading on on-chain investigation techniques and platform-level AML practices, see coverage of DeFi and how major exchanges monitor Ethereum flows.