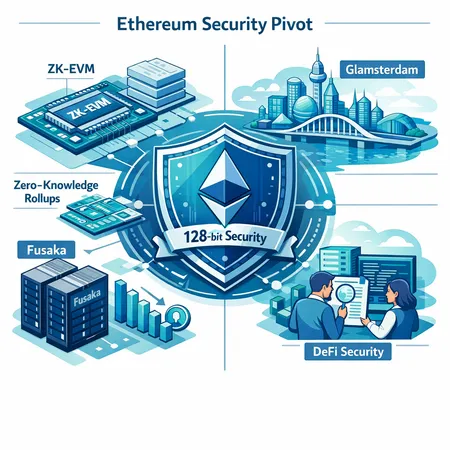
Ethereum's Security Pivot: 128‑Bit ZK‑EVMs, Fusaka, and the Road to Glamsterdam
Summary
Executive overview — why Ethereum is reprioritizing security
Ethereum’s roadmap for the coming years is less about chasing raw transactions-per-second and more about cryptographic certainty. The Foundation and broader research community have signaled a concrete goal: deliver 128‑bit provable security guarantees for ZK‑EVMs by 2026. That shifts many design decisions—proof system parameterization, circuit construction, verifier/publisher economics—toward strong, measurable soundness at the cost of some throughput or developer friction in the near term.
At the same time, protocol-level engineering work like the Fusaka upgrade has reduced node operating costs, lowering the operational barrier to participation. Combined with the proposed Glamsterdam set of upgrades across core layers, the net result should be a more secure, more decentralized platform—if the community manages trade-offs well.
Below I unpack what 128‑bit security means in practice, why it matters for ZK‑EVMs and rollups, how Fusaka and Glamsterdam affect decentralization, and what each type of stakeholder needs to do to prepare.
What “128‑bit provable security” actually means for ZK systems
In practical terms, 128‑bit security is a widely accepted industry benchmark: an adversary's chance of breaking cryptographic assumptions should be on the order of 2^-128—effectively infeasible with present and near-term computing resources. For ZK‑EVMs this covers multiple layers:
- Proof soundness: Probability that an invalid state transition produces a valid proof must be ≤ 2^-128. In protocol terms, this means choosing proof systems, hash functions, and randomness generation with proven or well-accepted bounds.
- Collision and preimage resistance: Hash schemes used inside circuits (for commitments, Merkle proofs, etc.) need bit-strength consistent with 128‑bit security.
- Complexity assumptions: Algebraic assumptions behind SNARK/STARK constructions must be parameterized to yield 128‑bit security margins.
Achieving these guarantees is not free. Higher security targets normally increase parameter sizes, proof construction complexity, or both—so developers and protocol designers face trade-offs in proving time, proof size, and verifier cost. The Foundation’s roadmap acknowledges that: the emphasis is on provable security rather than ad-hoc performance gains (CryptoNews report on the 2026 deadline; CryptoBriefing summary of the roadmap).
Why this matters for ZK‑EVM rollups and DeFi security
Zero-knowledge rollups will be the primary beneficiaries — and the primary vector for changed risk calculations.
- Stronger settlement finality: ZK proofs that meet 128‑bit soundness reduce the need for long withdrawal delays or multi-week fraud-proof windows. For DeFi platforms, that lowers funds-at-risk tied to long challenge periods and accelerates asset mobility between L1 and rollups.
- Lower systemic trust: With high-confidence cryptographic finality, the economic security of rollups becomes less dependent on the honesty assumptions of sequencers or trust-minimized censorship-resistant designs. That’s good for capital efficiency and composability.
- New attack surface: Conversely, increasing cryptographic complexity concentrates risk on the correctness of proof compilers, circuit libraries, and zk-tooling. A subtle bug in a shared proving library could have outsized DeFi systemic effects.
DeFi risk managers should therefore perform a two-axis reassessment: measure both the reduction in traditional fraud-risk exposure and the increase in cryptographic-implementation risk. This dual view often requires different assessment tools—code-level proof audits, incentivized bug bounties focused on proof generators, and operational checks on prover key material.
ZK‑EVM teams that prioritize 128‑bit proofs will face short-term performance costs (longer proof times, larger prover hardware needs). But as research and engineering progress, many of these costs can be mitigated; the trade is explicitly front-loaded.
Fusaka: lowering node costs and why that matters for decentralization
The Fusaka upgrade—which reduced multiple node operating costs and prepared the chain for subsequent improvements—has concrete, cascading effects on participation economics and decentralization. Reporting on Fusaka highlights cost reductions for node operators and previews the next combined upgrade, Glamsterdam (TokenPost on Fusaka).
Why node cost matters:
- Barrier to entry: Lower storage, bandwidth, and CPU requirements mean more independent teams and smaller operators can run full nodes and validators. That increases the number of read-and-verify points across the network.
- Economic resilience: More nodes dilute the concentration risk associated with a small number of large providers (cloud or institutional).
- Operational diversity: With lower cost, a broader ecosystem of infra providers, regional operators, and community-run nodes can flourish, which helps censorship resistance and improves observability for DeFi risk teams.
Fusaka’s gains are foundational: they make it practical to aim for stronger cryptographic guarantees while keeping the network sufficiently decentralized. If proving becomes costlier to achieve 128‑bit margins, having many low-cost full nodes improves protocol resilience by enabling diverse verification and monitoring paths.
Glamsterdam: combining upgrades across core layers
Glamsterdam is presented as a coordinated set of changes touching multiple core layers (execution, consensus, and network/infrastructure). The aim is to harmonize throughput, verifiability, and long-term upgradeability so that cryptographic security targets don’t come at the expense of liveness or decentralization.
Key objectives often discussed in engineering threads and community summaries include:
- Standardized verifier interfaces so L1 and rollups can agree on interoperable proofs and security parameters.
- Consensus-level tweaks to better support ZK proof publishing and efficient proof verification at scale.
- Network and node improvements borrowed from work like Fusaka to keep full-node participation affordable.
Put simply, Glamsterdam is meant to be the “glue” that allows 128‑bit ZK security goals to be realized without breaking the rest of the stack. It coordinates assumptions so that developers, provers, and validators share a common security baseline.
Operational implications by stakeholder
DeFi risk managers
- Recalculate time-based exposure metrics: shorter withdrawal windows could reduce capital locked in insurance or time-based hedges.
- Add cryptographic dependency checks to due diligence: audit proof compilers, circuit libraries, and the prover infra used by protocols.
- Build monitoring for proof publication and verifier metrics (latency, failed-verification counts) to spot degraded soundness.
Validator and node operators
- Expect evolving hardware needs: provers may need more memory or specialized CPUs/GPU work for efficient proof generation if live proving becomes common. But Fusaka’s cost reductions offset some of this by lowering base node costs.
- Tune software stacks for hybrid roles: nodes may both serve standard consensus duties and support rollup proof distribution/verification.
- Consider geographic and cloud-hybrid deployment to keep operational diversity high and cost-effective.
Developers and security engineers
- Prioritize portable correctness in circuit design: small library bugs can cascade across rollups and L2 apps.
- Contribute to formal verification and soundness proofs where feasible, or at least integrate fuzzing and property-based testing in the zk toolchain.
- Plan for longer test and canary periods when moving to 128‑bit parameter sets—both proving and verification costs will change.
Timeline and practical recommendations (through 2026)
- Short term (now–18 months): Audit current zk libraries, add runtime checks, and participate in testnets targeting the Foundation’s recommended parameter sets. Prepare proving infra budgets; test with larger parameterized circuits.
- Medium term (18–36 months): Participate in canary deployments that adopt 128‑bit settings. Validators and infra teams should rehearse upgrades and monitor proof-publishing flows. DeFi teams should stage migratory paths for assets and liquidity to ZK rollups that meet higher security baselines.
- By 2026: Expect mainstream ZK‑EVM implementations to claim 128‑bit provable tail risks. At that point, production readiness depends more on ecosystem tooling, proof-verifier integration at L1, and the maturity of Glamsterdam-specified interfaces.
Practical checklist:
- Security engineers: require proof-circuit audits and integrate prover fuzzing into CI.
- Builders: measure both user latency and security parameter impacts; make explicit choices when configuring rollups.
- Risk teams: run scenario analysis for both fraud-based and cryptographic-implementation failures.
Open challenges and trade-offs
- Performance vs. security: Stronger cryptographic margins increase costs and may slow iteration. That’s an engineering trade-off more than a binary win.
- Concentration of expertise: As zk tooling becomes more specialized, expertise may centralize—creating a social-centralization risk alongside the technical decentralization gains from Fusaka.
- Supply-chain risks: Key-generation ceremonies, prover hardware suppliers, and shared circuit libraries become high-impact dependencies.
Conclusion — operational posture for a security-first Ethereum
Ethereum’s pivot toward provable, 128‑bit ZK security is a deliberate move to lower existential protocol risks and raise trust for high-value DeFi activity. Fusaka’s cost reductions and the coordinated intent behind Glamsterdam make the 128‑bit target achievable without sacrificing decentralization—if the community invests in tooling, audits, and diversified infra.
For developers and security engineers: focus on correctness, auditability, and reproducible proving. For node operators and validators: tune for hybrid roles and prepare hardware and deployment strategies. For DeFi risk managers: update models to capture cryptographic-implementation risks alongside the reduced fraud windows.
The endgame is a more resilient, composable Ethereum where high-assurance cryptography underpins economic activity. It will require deliberate, cross-disciplinary work—cryptographers, protocol engineers, node operators, and risk teams working in concert. Bitlet.app and other infrastructure providers will be watching these changes closely, as they will materially affect custody, settlement, and P2P exchange patterns on ETH.
Sources
- CryptoNews: Ethereum shifts focus from speed to security with new 2026 deadline — https://cryptonews.com/news/ethereum-shifts-focus-from-speed-to-security-with-new-2026-deadline/
- CryptoBriefing: Ethereum security roadmap 2026 — https://cryptobriefing.com/ethereum-security-roadmap-2026/
- TokenPost: Fusaka upgrade reduced node costs and previews Glamsterdam — https://www.tokenpost.com/news/technology/18037
For broader context on how rollups reshape asset risk, see discussions on DeFi design and, for cross-market perspective, how different base-layer priorities have influenced markets such as Bitcoin.