Quantum Threat to Blockchains: Timeline, Post‑Quantum Defenses, and a Migration Roadmap
Summary
Executive summary
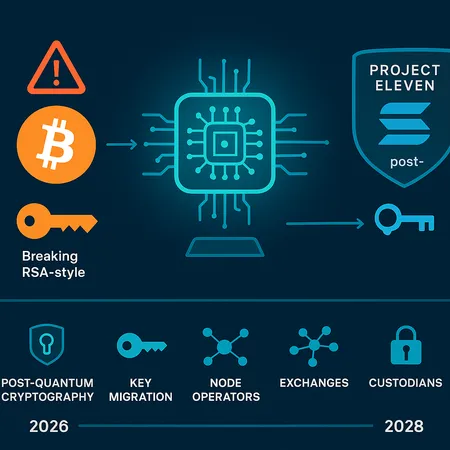
Quantum computing is no longer just a physics lab headline; it is a practical risk vector for blockchain cryptography that security teams must plan for now. Several research and industry voices argue a realistic danger window exists in the 2026–2028 timeframe unless networks adopt post‑quantum mitigations. At the same time, other leaders see quantum as a catalyst to strengthen protocols through upgrades and hybrid cryptography. This explainer translates those timelines into technical risk, reviews active defenses (including Solana’s Project Eleven), and lays out an actionable migration roadmap for CTOs, security leads, node operators, exchanges and custodians.
Why the 2026–2028 timeline matters
Estimates vary, but a growing chorus of analysts suggests that if error budgets and engineering delays accumulate, a capable adversary could threaten practical key recovery by the mid‑to‑late 2020s. Reporting that frames the risk window around 2026–2028 highlights both the hardware scaling trajectory and the time needed for protocol upgrades and ecosystem testing. See the timeline summary and urgency discussed by security analysts at Crypto.NEWS warning article.
Why is this timeframe actionable? Because real-world migration of keys, wallets, exchanges and consensus rules is slow—planning, implementation, audits and coordination across a decentralized network can take years. That gap between theoretical breakage and practical readiness is precisely what makes the 2026–2028 window a policy and engineering priority.
How quantum actually threatens blockchains (technical primer)
Most public blockchains—including BTC and many others—rely on elliptic‑curve cryptography (ECDSA/ECDH variants) for signatures and key agreement. A sufficiently powerful quantum computer running Shor’s algorithm would be able to derive a private key from a public key in polynomial time. Practically that means:
- Any address whose public key has been broadcast (for instance, after a spend) becomes a target: an attacker could compute the private key and drain funds before a transaction confirms.
- Transaction replay windows and mempool latency become attack surfaces: even a few seconds can be enough for a quantum adversary with network access.
- Long‑term confidentiality of keys used for multisigs, node TLS, or cross‑chain bridges could be compromised retroactively if encrypted artifacts are recorded today and broken later.
A separate threat axis is Grover’s algorithm, which roughly halves the effective security of symmetric primitives. That is manageable by doubling key sizes, but asymmetric algorithms require redesign or replacement.
What “post‑quantum resistance” means in practice
Post‑quantum cryptography (PQC) refers to classical cryptographic algorithms believed to resist both classical and quantum attacks. For blockchains, PQC has two principal dimensions:
- Post‑quantum signatures: Replacing or augmenting ECDSA-style signatures with algorithms such as lattice‑based schemes (e.g., CRYSTALS‑Dilithium) or stateless hash‑based signatures (e.g., SPHINCS+). Tradeoffs include signature size, verification cost, and statefulness.
- Post‑quantum key exchange / KEMs: Reworking protocols that rely on Diffie‑Hellman-type agreements to use KEMs that are secure against quantum adversaries.
Common deployment strategies for blockchains are:
- Hybrid signatures/KEMs: Combine an existing classical signature with a PQC scheme, requiring an attacker to break both to forge a valid signature. This is a near‑term pragmatic approach for incremental migration.
- Full migration: Replace the signature scheme network‑wide via a hard fork or upgrade to a PQC-only algorithm—operationally heavier and riskier, but simpler in the long run.
- Layered mitigation: Limit exposure by avoiding address reuse, pushing funds to PQC‑protected addresses, and reducing any broadcast of public keys until PQC is in place.
Each approach has tradeoffs around performance, blockchain bloat (larger signatures), and backward compatibility.
Concrete industry responses: Solana’s Project Eleven and other practical steps
Not every project is waiting for consensus friction. The Solana Foundation recently announced a partnership with Project Eleven to harden parts of the Solana stack against quantum threats—an example of a proactive, ecosystem‑level defense. Details and the foundation’s approach are summarized in reporting on the initiative here.
Solana’s steps illustrate a layered strategy:
- Research and integration of PQC algorithms where latency and throughput constraints allow.
- Engineering milestones to test hybrid signature schemes in controlled environments.
- Collaboration with cryptographers, hardware vendors, and validators to pilot upgrades before mainnet deployment.
These are instructive for other ecosystems because they show that early R&D, incremental rollouts, and cross‑stakeholder coordination reduce upgrade risk.
Differing industry views: alarm, pragmatism, and optimism
Public statements on quantum vary. Some analysts urge rapid defensive action to avoid the 2026–2028 pressure window. Others, including well‑known industry figures, argue quantum will ultimately strengthen — not break — major assets by forcing upgrades and modernization. For example, Michael Saylor has publicly suggested that quantum computing could make Bitcoin stronger over time by compelling improvements to the protocol and infrastructure. See Saylor’s comments in coverage by Benzinga here.
That optimism is defensible if the ecosystem invests early in standards, libraries, wallets and testing. But optimism without engineering pipelines and governance readiness is risky. The difference between theoretical resilience and operational resilience is execution—hence the value of concrete migration roadmaps below.
Practical roadmap for node operators, exchanges and custodians
This section translates risk into prioritized actions with timelines suitable for teams who must deliver before the 2026–2028 window.
Immediate (0–12 months)
- Inventory and classification: Compile a full inventory of keys, signing endpoints, address types and pubkey exposure vectors across operational systems, wallets and cold storage. Prioritize high‑value and high‑exposure assets.
- Reduce exposure: Stop or minimize address reuse; sweep funds from addresses with exposed public keys (e.g., spent P2PK outputs). For many traders, Bitcoin UTXOs that already revealed public keys should be high priority.
- Establish a PQC working group: Cross‑team forum with cryptographers, devops, legal and product to own the PQC migration plan.
- Start vendor and dependency audit: Ensure hardware wallets, HSMs and signing libraries have PQC support roadmaps.
Near term (12–24 months)
- Prototype hybrid signing: Implement hybrid signatures in testnets and internal systems. For performance‑sensitive chains such as Solana, run stress tests and measure throughput and fee implications.
- Key‑management upgrades: Extend HSM policies to support multi‑key types, versioning, and cold key generation for PQC keys. Practice offline key generation and secure key migration flows.
- Exchange hot/cold segregation: Exchanges should maintain hot pools with minimal balances and plan bulk migration windows for cold reserves to PQC‑protected addresses.
- Legal and compliance: Update custody SLAs and incident response playbooks to include quantum‑threat scenarios.
Medium term (24–48 months)
- Network upgrades and governance: Work through upgrade proposals, testnets and node client changes. For BTC this will be slow and conservative; for faster governance models the window is shorter.
- Full migration pilots: Move a subset of real funds onto PQC/hybrid addresses under live conditions with multisig and time‑lock protections.
- Monitoring and detection: Deploy telemetry to detect anomalous pre‑signature or pre‑broadcast key scraping attempts.
Long term (48+ months)
- Finish migration and retire legacy keys where safe.
- Maintain a PQC update cadence as standards evolve (NIST and other standard bodies may update recommendations).
- Conduct regular drills simulating a quantum‑capable adversary.
Key migration patterns and cryptographic recommendations
- Hybrid signatures as a default near‑term approach: Require both an ECDSA (or ECDSA-like) signature and a PQC signature. An attacker must break both to succeed.
- Use lattice‑based PQC (e.g., Dilithium) for general purpose, but account for signature size and verification cost. Use hash‑based schemes (SPHINCS+) where stateful or high‑assurance signatures are required, accepting larger signatures.
- Staggered rollouts: Generate new PQC keys and perform test transfers before mass migration. Avoid bulk mass broadcasts that could temporarily expose keys.
- Multi‑sig rekeying: For multisig setups, reconfigure M-of-N schemes to include PQC keys gradually, maintaining redundancy and recovery paths.
- Hardware integration: Engage HSM and hardware‑wallet vendors early; ensure PQC key formats and signing flows are standardized between software and hardware.
Governance, forks and coordination considerations
Different chains require different governance approaches. Bitcoin’s conservative upgrade path means community consensus, broad client implementation and miner/validator coordination are necessary—this lengthens the timeline. A coordinated technical roadmap, transparent specification drafts, and testnet milestones reduce the risk of rushed or contentious upgrades.
For faster‑moving ecosystems, the danger is fragmentation: ad‑hoc PQC choices could produce incompatible forks or security gaps. A recommended industry approach is alignment on hybrid patterns and a small set of vetted PQC algorithms to reduce fragmentation.
Actionable checklist for CTOs and security leads (quick reference)
- Inventory and classify all keys and address types; map pubkey exposure.
- Prioritize migration of high‑value and publicly exposed addresses.
- Stand up a cross‑functional PQC working group.
- Build and test hybrid signature support in non‑production environments.
- Update HSM/HW wallet vendor roadmaps and stress test PQC integrations.
- Plan governance and upgrade pathways with community stakeholders early.
- Run tabletop exercises simulating a pre‑emptive quantum key compromise.
- Track NIST PQC standards and public implementations; keep a patch/update window for libraries.
Final thoughts: risk is real, but manageable with planning
Quantum computing will force cryptographic evolution across the industry. The 2026–2028 risk window signaled by some analysts is not a doomsday clock but a call to action: timelines are short for complex ecosystems. The positive signal is that projects like the Solana Foundation’s partnership with Project Eleven show practical, early hardening is possible and that industry actors can collaborate on safe migrations. At the same time, the conservative upgrade model of Bitcoin and the community’s governance realities mean custodians and exchanges must prioritize operational mitigations now.
Engineering, governance and clear migration roadmaps will determine which ecosystems adapt smoothly and which ones face avoidable operational risk. Start with inventory and exposure reduction, then move toward hybrid cryptography pilots, vendor integration and coordinated network upgrades. Simple steps taken today—address hygiene, key rotation policies, and a tested PQC plan—will materially reduce the odds that funds or identity material become vulnerable in a near‑term quantum scenario.
Bitlet.app and other custody and exchange platforms should be thinking about these processes now: the costs of planning and testing are small compared with the risk of being forced into emergency migrations under adversarial pressure.
Sources
- Crypto.NEWS, "Bitcoin faces Q‑day risk if quantum threat isn’t patched by 2026–2028": https://crypto.news/bitcoin-faces-q%e2%80%91day-risk-if-quantum-threat-isnt-patched-by-2026-2028/
- Bitcoinist, "Solana Foundation plan to combat quantum computing" (Project Eleven): https://bitcoinist.com/solana-foundation-plan-to-combat-quantum-computing/
- Benzinga coverage of Michael Saylor on quantum computing and Bitcoin: https://www.benzinga.com/crypto/cryptocurrency/25/12/49440904/michael-saylor-says-quantum-computing-will-make-bitcoin-stronger-not-break-it-whats-his-rea?utm_source=benzinga_taxonomy&utm_medium=rss_feed_free&utm_content=taxonomy_rss&utm_campaign=channel&utm_source=snapi