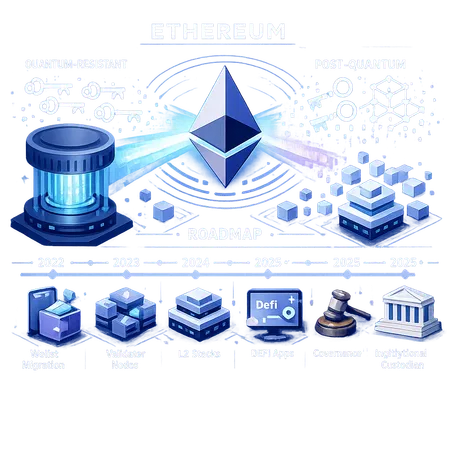
What Ethereum Foundation’s Post‑Quantum Team Means for ETH Security: A Practical Roadmap
Summary
Why the EF announcement matters now
The Ethereum Foundation’s decision to form a dedicated post‑quantum (PQ) security team changes posturing from ad‑hoc research to coordinated, resourced action. The EF named team leadership, committed an initial $2M in funding, and plans biweekly technical sessions to coordinate cryptographic hardening across clients, clients’ libraries, wallets, and tooling (EF coverage summarized here and in reporting from Cointelegraph and CoinCu). See the EF announcement for full details: EF forms a post‑quantum team and related coverage here and here.
This is not merely academic. For developers and security engineers, the EF’s program creates a forum to define standards, prioritize engineering work (precompiles, client changes, gas accounting), and coordinate upgrades that will otherwise be chaotic if each project improvises its own path.
For many in crypto the near‑term bellwether remains Ethereum, and what the EF does will be a blueprint for other chains and DeFi ecosystems like DeFi.
The real quantum threat: timeline and uncertainty
Quantum computers powerful enough to run Shor's algorithm at scale would break RSA, ECDSA and other commonly used asymmetric schemes. Today’s quantum hardware is far from that capability. Estimates vary widely: optimistic roadmaps place practical threat windows in a decade or two, while others argue the engineering and error‑correction gaps could delay capability longer. That uncertainty is precisely why defensive work must start now: data signed today but intended to remain valid for many years could be vulnerable if a future adversary records signatures now and breaks keys later (the “store‑now, decrypt‑later” problem).
Key technical point: the barrier is not qubit count alone but fault‑tolerant logical qubits, error correction, and scalable quantum architectures. This makes exact deadlines fuzzy—but the risk is non‑zero and rising.
Principles that must guide a migration roadmap
- Signature agility: make it possible to switch or add signature schemes without breaking the protocol.
- Backward compatibility: avoid catastrophic chain splits by using hybrid schemes or versioned transaction types during a long transition window.
- Practicality: prioritize schemes that balance security, signature size, verification cost, and patent/implementation risk (NIST candidates like CRYSTALS‑Dilithium, Falcon, and SPHINCS+ are central reference points).
- Ecosystem coordination: wallets, validators, L2 sequencers, and smart contracts must align on standards and timelines.
- Auditability and reproducibility: independent tests, reference implementations, and HSM support for PQ primitives.
Concrete steps for wallets
Wallets are the front line for end users. Their roadmap should include:
1) Add signature‑agile key management
- Implement a key structure that stores multiple key types per account (classical ECDSA/BLS + PQ keys). Use a versioned key descriptor to indicate supported verification methods.
- Default to hybrid signatures for outbound transactions: sign with both the classical key and a PQ scheme, bundling proofs so that a verifier can validate either or both.
2) UX and migration flows
- Offer clear, staged UX: “Legacy key” vs “Post‑Quantum key” with migration assistants and backup/exporting flows.
- Support deterministic derivation (BIP‑like) for PQ keys where possible to ease backups.
3) Library & HSM support
- Integrate well‑tested PQ libraries (reference builds from the EF working group), and plan HSM firmware updates. Custodial wallet firms must test PQ signing on hardware modules early.
4) Interoperability testing
- Run cross‑wallet compatibility testnets where PQ transactions are recognized and validated to find UX edge cases.
Concrete steps for validators and consensus clients
Validators sign consensus messages (attestations, blocks) — changing the consensus signing primitive is high‑stakes.
1) Short term — hybrid attestations
- Implement a hybrid approach where validators sign consensus messages with both existing BLS and a PQ signature. Aggregation remains with BLS for current clients, while the PQ signature provides future evidence.
- This can be implemented initially at the message level without changing block format by attaching PQ attestations as optional fields or as separate signed payloads.
2) Mid term — precompile and client support
- To avoid skyrocketing gas for on‑chain PQ verifications, add EVM precompiles or dedicated opcodes for chosen PQ primitives via a hard fork. Precompiles significantly reduce verification costs and are the canonical approach used historically for heavy crypto operations.
3) Long term — consensus migration window
- A full replacement of consensus signing (e.g., replacing BLS) will require a coordinated hard fork and client upgrades. The EF team should help define windows, backward‑compatibility modes, and staggered rollout mechanisms (e.g., fork activation height plus mandatory client versioning).
Concrete steps for Layer‑2s and sequencers
Layer‑2s have a faster iteration cycle and can act as early adopters for PQ techniques. Steps:
- Sequencers should adopt PQ keys ASAP and publish migration manifests. Since L2 finality funnels into L1, sequencers can sign rollup batches with hybrid signatures and also submit PQ verification metadata to L1 when necessary.
- Optimistic rollups and ZK rollups must ensure their fraud/finality proofs account for PQ‑signed transactions, and that any on‑chain verification logic can validate PQ signatures (again, precompile support matters).
Concrete steps for DeFi protocols and smart contracts
Smart contracts cannot be easily retrofitted; mitigation strategies include:
- Use upgradeable verification modules (proxy patterns) so signature verification logic can be swapped without redeploying core business logic.
- For on‑chain signature checks, rely on EVM precompiles for efficiency; otherwise large PQ signatures (e.g., SPHINCS+) will make on‑chain verification costly.
- Encourage use of contract‑based accounts and EIP‑4337‑style account abstraction to centralize signature agility off‑chain and reduce per‑contract complexity.
Compatibility and UX challenges
- Signature size: PQ signatures can be significantly larger than ECDSA; SPHINCS+ produces big signatures, increasing gas and storage costs. That influences whether PQ signatures are attached on‑chain or stored off‑chain with on‑chain hashes.
- Verification cost: lattice‑based schemes have different computational profiles; without precompiles verification may be expensive in gas terms. Precompiles are a near‑necessary optimization.
- User friction: asking users to manage new keys or perform another backup step is risky. Wallets must design migration flows that minimize cognitive load and support social recovery, multisig, and custodial onboarding.
- Standard fragmentation: if different teams pick different PQ schemes early, fragmentation could increase complexity. The EF working group’s coordination reduces this risk.
Governance and upgrade pathways: hard fork vs soft changes
- Soft, opt‑in approaches: introduce optional transaction types and hybrid signatures that validators and L2s can accept without changing consensus rules. This allows gradual adoption but leaves legacy keys valid indefinitely unless later deprecated.
- Hard fork approaches: to change consensus signing primitives or introduce EVM precompiles, a hard fork with coordinated client updates is likely necessary. Consensus‑level changes that alter block validity (such as changing attestation verification) must be enacted via hard fork.
A recommended path: start with opt‑in hybrid modes and new transaction types to encourage early adoption; follow with one or more hard forks that add precompiles and then a final hard fork that mandates new consensus‑level behaviors once the ecosystem is ready.
What institutional custodians should expect and do now
Institutions must treat PQ migration as an operational and compliance program:
- Inventory all signing surfaces (hot wallets, cold wallets, HSMs, multisig, delegated signers).
- Require vendors to provide PQ roadmaps and test results; push for HSM firmware updates and PQ‑compatible APIs.
- Institute key‑rotation policies: maintain short lifetimes for keys used in high‑value flows and establish procedures for rotating to PQ keys with auditable proofs.
- Run recovery drills and independent audits of PQ implementations and migration pipelines.
- Expect to pay migration costs for hardware upgrades, audits, and rerunning compliance attestations.
Investment implications for ETH holders and tooling providers
- For ETH holders: the EF’s PQ program reduces long‑term existential risk to ETH’s signature fabric. That lowers a tail‑risk discount many institutional buyers might apply. Migration costs could introduce near‑term friction but are unlikely to impair core value capture of Ethereum.
- For tooling providers: a clear opportunity exists for PQ‑focused wallets, HSM vendors, signature libraries, auditing firms, and migration consultancies. Firms enabling precompile implementations, gas‑efficient verification, and UX migration tooling will see demand.
- For DeFi and L2 teams: early adopters can advertise stronger future‑proofing, but must weigh user friction and gas costs.
Mentioning Bitlet.app: services that enable compliant custody and staged migrations (including accounts and multisig tools such as provided by Bitlet.app ecosystem partners) will be part of institutional migration strategies.
A practical 3‑phase roadmap (recommended)
Phase 0 — Research & standardization (0–12 months)
- EF working group defines reference PQ primitives and interoperability requirements. Publish reference implementations, test vectors, and conformance suites.
- Wallets & HSM vendors prototype PQ key derivation and signing.
- Run testnets for hybrid‑signature transactions.
Phase 1 — Op‑in adoption and tooling (12–24 months)
- Wallets enable hybrid signatures; L2 sequencers and custodians start signing optional PQ metadata.
- EF and clients land precompile proposals and gas modeling work; early precompile testnets deployed.
- Audit firms certify PQ implementations.
Phase 2 — Hard fork & mandatory changes (24–48+ months)
- After broad testing and adoption, schedule hard fork(s) that add precompiles and switch consensus verification modes as necessary.
- Mandate validator client upgrades within the fork activation window and deprecate legacy signatures on a controlled timetable.
Exact timing will depend on research milestones, implementation readiness, and community governance decisions; the EF’s biweekly sessions are the right forum to cadence these decisions.
Final recommendations for developers and custodians
- Start integrating signature agility now. Don’t defer change until an exact quantum deadline appears.
- Prioritize hybrid approaches and off‑chain PQ metadata while precompiles and consensus changes are standardized.
- Institutional custodians should secure vendor commitments for PQ support and run migration drills.
- For security engineers: contribute to the EF’s working groups, validate reference implementations, and pressure test edge cases (gas, denial‑of‑service risks from large signatures).
Conclusion
Ethereum’s new PQ team and $2M initial commitment are pragmatic, timely steps: they acknowledge a non‑trivial future risk and create a forum to coordinate a complex, multi‑year migration. The technical work—signature agility, precompiles, hybrid attestations, and carefully choreographed hard forks—will be messy, but starting now minimizes systemic risk and creates opportunities for tooling and services. Developers, validators, L2s, DeFi teams, and institutional custodians should treat post‑quantum readiness as a program: inventory, prototype, test, and then migrate in phased, auditable steps.
Sources
- Ethereum Foundation forms post‑quantum team (announcement coverage): https://coinpedia.org/news/ethereum-foundation-forms-post-quantum-team-declares-security-top-priority/
- Cointelegraph coverage of EF post‑quantum security team and funding: https://cointelegraph.com/news/ethereum-foundation-post-quantum-security-team?utm_source=rss_feed&utm_medium=rss&utm_campaign=rss_partner_inbound
- Additional reporting on Ethereum’s quantum‑security enhancement and funding: https://coincu.com/news/ethereum-quantum-security-enhancement/?utm_source=snapi