Ethereum's Fusaka Upgrade: Enhancing Scalability, Security, and What to Expect in 2025
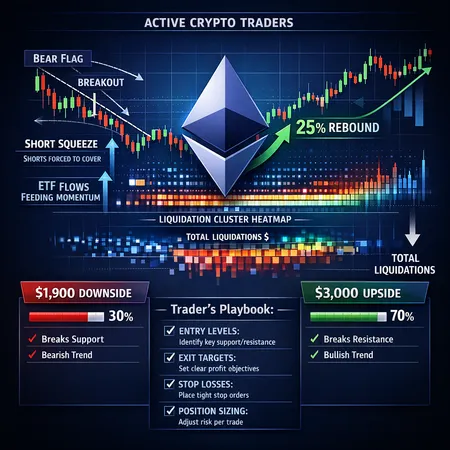
Ethereum continues to evolve with its much-anticipated Fusaka upgrade, designed to improve scalability and security on the network. This upgrade seeks to reduce congestion, optimize transaction speed, and strengthen the overall security framework, which could positively influence Ethereum's price throughout 2025.
Scalability remains a critical focus, as increased transaction throughput will make Ethereum more efficient and accessible for decentralized applications and users. Enhanced security features will safeguard the network against vulnerabilities and attacks, fostering greater trust in Ethereum's ecosystem.
For crypto investors and enthusiasts, the Fusaka upgrade marks a pivotal moment. Improved network performance can drive adoption, potentially boosting Ethereum's market valuation. However, as always, it is essential to stay informed and consider market dynamics when making investment decisions.
If you're interested in growing your crypto portfolio with Ethereum or other assets, platforms like Bitlet.app offer innovative services such as Crypto Installments. This feature allows you to buy cryptocurrencies now and pay monthly, making entry more affordable and convenient.
Stay tuned for more updates on Ethereum's Fusaka upgrade and leverage tools like Bitlet.app to make the most of emerging opportunities in the crypto space.