Post‑Mortem: Upbit’s Solana Hot‑Wallet Breach — Technical Causes, Response, and Market Impact
Summary
Executive summary
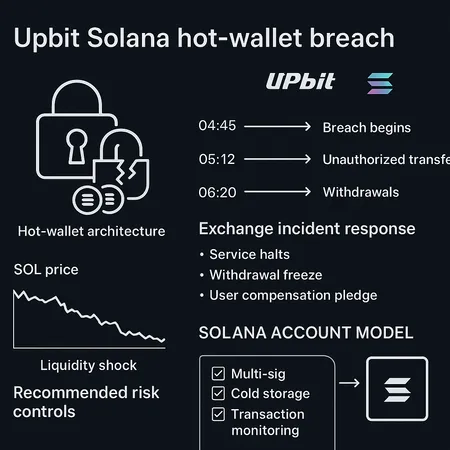
Upbit's Solana hot‑wallet incident — reported between roughly $36M and $38.8M in losses — is a vivid example of how a single compromised signing key or operational mistake can lead to large, rapid on‑chain outflows on high‑throughput chains. Upbit halted Solana transfers, froze withdrawals, and pledged to cover customer losses while investigating the root cause. This post‑mortem breaks the chronology, explains how hot‑wallet architecture and Solana's account model shaped both the failure and the response, reviews immediate market effects on SOL, and lists concrete controls traders and custodians should demand from exchanges.
Chronology: what we know so far
- Initial reports surfaced that Upbit experienced an abnormal, rapid outflow of SOL from an exchange hot wallet. Early coverage put the figure in the mid‑$30M range; Blockonomi reported a $36M loss and suspension of services, while other outlets documented figures up to $38.8M and operational halts.
- Upbit responded by halting Solana transfers and freezing withdrawals to stop further outflows; multiple outlets confirmed the withdrawal freeze and transfer halt as the immediate mitigation step (Coinpaper, Blockonomi).
- As investigators and on‑chain watchers tracked movements, exchange executives communicated intent to cover customer losses and pledged continuity of services as the probe continued (CryptoPotato).
- Price commentators documented immediate selling pressure and technical resistance levels for SOL in the hours and days after the exploit (CoinPedia analysis).
Each of the cited articles fills in pieces: confirmation of the transfer halt and operational interruption, the on‑chain outflows, and public promises to cover losses.
Technical anatomy: hot‑wallet architecture and Solana’s account model
Why hot wallets fail fast on Solana
Hot wallets are, by definition, online signing capabilities that allow an exchange to process withdrawals, internal transfers, and market operations quickly. On Solana, the combination of an account‑based token model (SPL token accounts/associated token accounts), low fees, and very fast finality means that once an attacker has a signing key or an exploitable operational vector, funds can be moved and finalized in seconds.
Key facts to keep in mind:
- Signer = control: SPL tokens live in accounts owned by a public key (or PDA); anyone who can produce valid signatures for the controlling key can move tokens. If a hot key is leaked or an HSM/MPC is bypassed, transactions are valid and final.
- High throughput, low friction: Solana's performance makes drains quicker and cheaper than on many chains, reducing the window for human intervention.
- Account proliferation: Each token requires its associated token account (ATA), increasing operational surface area; rebuilding or reassigning ATAs during an incident is non‑trivial.
Mitigations available within Solana’s model
Solana supports programmatic constructs that can reduce single‑key risk if used correctly:
- Program Derived Addresses (PDAs) and program‑controlled accounts: funds can be held under program logic that enforces multi‑party approval or time locks, avoiding single private keys owning large balances.
- SPL multisig programs: multi‑signature wallets can be used to require multiple signers for a withdrawal.
- On‑chain timelocks & guard contracts: custom programs can implement timelocks, withdrawal windows, or rate limits enforced at the protocol level.
However, these tools are only effective when correctly implemented and integrated with off‑chain operations. Many exchanges historically favor operational simplicity (single hot key signing by HSM/MPC) for performance and throughput, which concentrates risk.
Attack vectors and plausible root causes (operational perspective)
While full attribution for Upbit’s incident is ultimately for its investigators to publish, common root causes in similar breaches include:
- Private key leakage: extraction from an insecure workstation, compromised admin credentials, or insider theft.
- HSM/MPC misconfiguration: incorrectly segmented signing authority or a software bug in the MPC layer.
- Supply‑chain/CI compromise: malignant code signing or deployment of compromised wallet software.
- Process failures: lax withdrawal limits, absent whitelisting, or missing pre‑transaction checks that allowed large outbound transactions.
On Solana, any of these lead to one outcome: an attacker signs transactions and routes funds off‑exchange with minimal friction.
Exchange incident response: what Upbit did and best practices
Upbit moved quickly to halt transfers and freeze withdrawals — a standard and necessary first step to prevent additional theft. Multiple outlets confirmed the halt and that Upbit pledged to make customers whole (Coinpaper, CryptoPotato).
Good incident response contains several components:
- Immediate containment: pause the impacted asset's deposits/withdrawals; rotate or freeze signing keys where possible.
- Forensic triage: capture logs, signers, and on‑chain transaction data; engage external forensic firms early.
- Customer remediation: decide publicly whether the exchange will cover losses and how — transparent timelines and funding sources reduce panic.
- Communication playbook: frequent, accurate updates to users and markets; silence fuels speculation.
- Post‑mortem and hardening: publish findings, remediate technical gaps, and apply third‑party audits.
Upbit's pledge to cover customer losses helps short‑circuit immediate contagion of confidence, but it also shifts focus to governance: how will reserves be audited, and how will future operational risk be priced by users?
Market effects: SOL price, liquidity, and trader behavior
The exploit produced short‑term selling pressure on SOL, as on‑chain outflows often translate into market sales either by attackers or as exchanges rebalance exposed books. Price analyses and intraday commentary noted increased downside pressure and technical resistance levels following the incident (CoinPedia analysis).
Immediate market effects typically include:
- Reduced liquidity for the affected token on the exchange that froze withdrawals, raising bid‑ask spreads.
- Sell pressure if stolen tokens are liquidated on other venues.
- Cross‑asset volatility as traders reassess counterparty risk and rebalance portfolios (sometimes moving funds to perceived safe havens such as Bitcoin or stablecoins).
Longer term, the market reaction depends on the clarity and credibility of the exchange’s remediation and whether the root cause points to systemic protocol weaknesses or an exchange operational lapse.
What this means for Solana's on‑chain security
The Upbit incident underscores a key distinction: the vulnerability was operational rather than an intrinsic cryptographic failure in Solana. Solana’s protocol can support stronger custodial patterns (PDAs, multisig, programmatic guards), but those patterns are not automatic — they require design and discipline.
Two implications:
- Protocol capability ≠ operational practice: Solana supports mitigations, but exchange engineering teams must adopt them.
- Ecosystem maturity matters: as large custodians integrate Solana, demand for audited multisig contracts, MPC integrations, and hardened HSM stacks will rise.
For DeFi engineers and custodians, the incident should be a prompt to review how custodial designs map to Solana primitives and to test emergency key‑rotation and fund‑recovery workflows under load.
Practical controls traders and custodians should demand
Active traders, security engineers, and custodians should insist on clear, testable guarantees from counterparties. Minimum requirements include:
- Proof of hot/cold split and small hot balances: ask for evidence (e.g., address lists and signed attestations) that hot wallets hold only operationally necessary amounts.
- MPC or HSM signing with attestation: require third‑party audits and evidence that private keys are not extractable from signing hardware.
- On‑chain withdrawal limits and timelocks: protocol‑level or programmatic rate limits on large transfers from custodial accounts.
- Whitelisting and outflow constraints: ability to require destination whitelists for large withdrawals and multi‑level approvals.
- Transparent insurance & compensation frameworks: explicit statements about whether the exchange will cover losses, the funding source, and the SLA for remediation.
- Real‑time on‑chain alerts: customers should be able to subscribe to address monitoring for sudden movements or large outflows.
- Regular third‑party audits and public post‑mortems: insist on published results and remediation timelines after incidents.
If an exchange resists these, traders should treat counterparty risk as elevated and hedge by diversifying custody.
Operational recommendations for exchanges and custodians
Security teams and CTOs should treat this class of incident as preventable with disciplined design and investment. Recommended hardening steps:
- Adopt MPC for hot signing, combined with hardware roots of trust and threshold signing, to remove single‑key points of failure.
- Implement programmatic safeguards on Solana: PDAs, SPL multisig, and time‑lock patterns for large balances.
- Keep hot‑wallet balances minimal, synchronized with real‑time treasury and risk dashboards.
- Build automated anomaly detection tied to pre‑defined thresholds that can stop suspicious transactions before signing.
- Maintain playbooks and rehearsals: regularly test key rotation, cold wallet restores, and public communications in simulated incidents.
- Maintain insurance and reserve funds that are pre‑cleared and auditable, and communicate them in advance.
These controls are operationally non‑trivial but cheaper than reputational and balance‑sheet damage from a large breach.
Closing thoughts
The Upbit Solana hot‑wallet breach is a reminder that high performance and low fees on a chain can be a double‑edged sword: great for users, unforgiving for custodians that mismanage key material. Exchanges can and should use Solana’s on‑chain features to reduce risk, but sound off‑chain key management, MPC/HSM, and operational discipline remain decisive.
For security engineers and risk officers, the incident should prompt concrete questions to counterparties and an immediate review of controls. Active traders and custodians ought to demand transparency, real‑time monitoring, and concrete remediation commitments before increasing exposure to any single custodian.
Bitlet.app users and platform architects alike will find that disciplined custody design, clear incident playbooks, and transparent communication are the best ways to preserve liquidity and trust after incidents like this.
Sources
- https://blockonomi.com/upbit-exchange-reports-36-million-loss-in-solana-hot-wallet-security-breach/
- https://coinpaper.com/12700/upbit-halts-solana-transfers-after-36-8-million-hot-wallet-breach?utm_source=snapi
- https://cryptopotato.com/upbit-loses-38-5m-in-sudden-solana-outflow-withdrawals-frozen/
- https://coinpedia.org/price-analysis/solana-price-faces-pressure-after-36m-upbit-exploit-can-bulls-clear-the-150-resistance/