On‑Chain Forensics
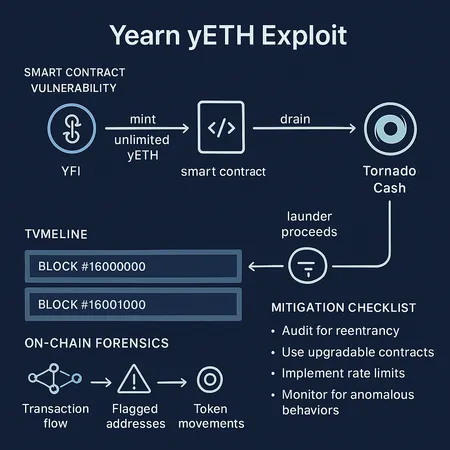
Post‑Mortem: How the Yearn yETH Exploit Minted Unlimited yETH and Raided the stETH/rETH Pool
A technical post‑mortem reconstructing how attackers minted unlimited yETH, drained a bespoke stETH/rETH pool, and laundered proceeds via Tornado Cash. Includes on‑chain forensic signals, timeline, vulnerability class, and mitigation checklist for DeFi engineers and risk officers.
Published at 2025-12-01 15:22:14
DeFi
All DeFi postsBitcoin
All Bitcoin postsLiquidity
All Liquidity posts- How US–Israel Strikes, an Oil Shock, and Strait of Hormuz Risk Are Roiling Bitcoin — What Traders Should Watch
- How U.S. Spot Bitcoin ETF Inflows Are Changing BTC Price Discovery and Liquidity
- Bitcoin's Tug-of-War: ETF Inflows Lift BTC to ~$68–70K — But Liquidity and a Multi‑Billion Options Expiry Threaten Volatility